Red Flags - Stay Alert and Stay Safe
Red Flags – Social Engineering
Identify Red Flags in an Email
Identifying red flags in an email is crucial to stay alert and stay safe from social engineering attacks. Here’s a breakdown of what to look out for:
Stay Alert: Red Flags From the Sender:
- First and foremost, check if the sender’s email address is unfamiliar or unrelated to your usual contacts.
- Additionally, scrutinize whether the email is from someone outside your organization, not related to your job responsibilities.
- Equally important is to assess if the email is from someone inside your organization, but the content is unusual or out of character.
- Furthermore, watch out for suspicious sender email domains, like “micorsoft support.com.”
- Moreover, consider if there’s a lack of personal acquaintance or endorsement from someone you trust.
- Take note if there’s no prior business relationship or communication history with the sender.
- Lastly, be wary of unexpected or unusual content, especially with embedded hyperlinks or attachments.
Stay Safe: Spotting Suspicious Hyperlinks:
- It’s important to mention that hovering over a hyperlink reveals a different destination URL, a significant red flag.
- Another key point is that emails with only long hyperlinks and no further context or content are suspicious.
- Additionally, be cautious of misspelled hyperlinks mimicking known websites, such as “www.bankofarnerica.com.”
Stay Vigilant: Identifying Unusual Recipients and Attachments:
- Consider whether you’ve been cc’d on an email to unfamiliar recipients.
- Additionally, be cautious of emails sent to an unusual mix of people, such as random groups or unrelated addresses.
- Look out for unexpected or nonsensical attachments, especially from senders who don’t typically send such files.
- Also, be cautious of attachments with potentially dangerous file types, with .txt files being the only inherently safe type.
Stay Aware: Timing, Subject Lines, and Content:
- It’s worth noting if emails are received at unusual times, especially outside regular business hours.
- Take note of irrelevant subject lines or subject lines that don’t match the email content.
- Similarly, be cautious of emails that appear as replies to unrequested or unsent messages.
- Pay attention to requests to click on links or open attachments under the threat of negative consequences or with promises of gain.
- Also, watch out for unusual or poor grammar and spelling errors in the email.
- Additionally, consider whether there are illogical or suspicious requests to click on links or open attachments.
- Trust your instincts if you sense discomfort or suspicion regarding the email’s content.
- Lastly, be cautious of emails requesting viewing of compromising or embarrassing images.
By being vigilant and attentive to these red flags, you can protect yourself and your organization from falling victim to social engineering attacks.
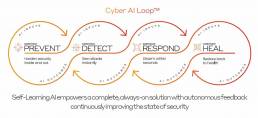
Enhancing Cybersecurity - Continuous Cyber AI Loop
Darktrace’s technology vision is a continuous, Cyber AI Loop™, where each capability autonomously feeds back into the system as a whole, continuously improving the state of cyber security.
Improving Awareness and Decision-Making
From the attacker's perspective, Darktrace PREVENT provides vital insights to defenders. Consequently, it enables them to identify existing devices that are externally facing or part of a critical attack path, enhancing their overall awareness of the environment.
Moreover, users benefit from contextual information about external facing assets and critical attack paths via tags in the DETECT and RESPOND user interface. This enables better decisions, quicker triage, and facilitates further modeling using this new information. For example, if PREVENT identifies a web server on a critical attack path, relevant entities receive tags in DETECT, providing crucial knowledge for detection modeling and AI Analyst investigations.
Incorporating Industry Standards for Faster Understanding
Darktrace incorporates the MITRE ATTACK Framework across the loop. Additionally, it tags devices identified by Darktrace PREVENT as sitting on a critical attack path with MITRE techniques corresponding to the inbound and outbound parts of the attack path. This provides automatic mapping to an industry-standard attack framework for auditing, compliance, and faster understanding of all components of the attack.
Richer AI Analyst Investigations
AI Analyst investigations become richer as they enrich existing investigations with malicious hostnames retrieved from PREVENT/ASM. Consequently, this indicates they are more likely to be suspicious and potentially part of an incident.
Heightening Email Security
Darktrace PREVENT/Attack Surface Management informs Darktrace/Email of potential threats, such as domain spoofing. This action heightens sensitivity around these assets and takes action when these spoof domains are used for malicious purposes. Hence, this leads to more accurate decision-making in the email realm, reducing analysis time for individual emails.
Consolidating Insights for Better Response
Assets confirmed as malicious by Darktrace PREVENT/Attack Surface Management automatically become ‘Watched Domains’ in Darktrace/Network. This enhancement enables security teams to consolidate insights from inside the business and externally on the attack surface in a single pane of glass, improving their ability to respond effectively.
Darktrace Prevent- Cyber Resilience Reinforcement
Darktrace Prevent
Hardens security Proactively
Identifies and prioritizes risks
Emulates attacks to test vulnerabilities
Helps organizations meet NIST and other regulations
Reinforcing Cyber Resilience with Darktrace PREVENT
In today’s rapidly evolving cybersecurity landscape, fortifying your defenses is paramount to safeguarding your organization against emerging threats. Darktrace PREVENT offers a proactive approach to cybersecurity, empowering organizations to anticipate and thwart future attacks.
Enhanced Visibility with Darktrace PREVENT/ASM
Darktrace PREVENT/ASM provides unparalleled visibility into your organization’s external exposure, enabling proactive risk identification and mitigation before an attack occurs. By continuously monitoring the external attack surface, PREVENT/ASM assesses all assets for risks, vulnerabilities, and threats, helping you stay one step ahead of potential attackers.

Darktrace PREVENT / Attack Surface Management™
Enter Darktrace PREVENT, an interconnected suite of AI products designed to provide proactive cybersecurity, helping organizations anticipate future cyber-attacks. This product family empowers CISOs and security staff to function as an AI-powered Red Team, simulating attacks, identifying critical assets, testing vulnerability pathways, and fortifying defenses to thwart attackers from compromising vital systems and data.
One component of Darktrace PREVENT is Attack Surface Management™ (ASM), which offers unparalleled visibility into the organization’s external exposure, enabling the security team to proactively identify risks before an attack occurs. ASM continuously monitors the external attack surface, assessing all assets for risks, high-impact vulnerabilities, and external threats. It is instrumental in revealing shadow IT, supply chain risks, potential phishing domains, vulnerabilities, misconfigurations, and risks associated with mergers and acquisitions. Additionally, ASM communicates its findings to Darktrace DETECT + RESPOND, enhancing sensitivity around critical chokepoints.
Darktrace PREVENT / End-to-End™
Attack Path Modeling
Maps the most relevant and impactful attack paths through your organization in real time.
Pentest Augmentation
Tests all potential attack pathways around the clock.
Breach & Attack Emulation
Deploys harmless “attacks” that emulate malware, phishing, spoofing, and other common threats.
Security & Awerness Training
Identifies users who are exposed or vulnerable to phishing, allowing IT teams to tailor training based on real-world data.
Cyber Risk Prioritization
Continuously updates its findings to show you which areas of focus would reduce risk to the greatest extent.

Darktrace Solutions Feed Back into the Cyber AI Loop™
Darktrace PREVENT forms part of Darktrace’s Cyber AI Loop, which orchestrates a set of dynamically related cyberthreat capabilities. Combined with Darktrace DETECT™ + RESPOND™, Darktrace PREVENT autonomously implements countermeasures to harden your defenses around critical vulnerabilities and attack paths.



