PS5 Repair - Comprehensive Solutions

Is your PlayStation 5 acting up? Trust Newtech to provide expert repair solutions tailored to your console’s specific needs. With our dedicated team of specialists, we prioritize restoring your gaming experience to its peak performance.
Common Issues We Address:
- Overheating Consoles: Is your PS5 running hotter than usual? Overheating can lead to performance issues and potentially damage your console. Let Newtech’s expert technicians diagnose and address heat-related issues to keep your PS5 running smoothly.
- Crashes & Freezing: Experiencing sudden crashes or freezing during gameplay can be frustrating. Our specialists quickly identify and resolve software issues to restore seamless gaming experiences without interruptions.
- Network Connectivity Problems: Struggling with PSN or Wi-Fi connectivity issues? Our team of experts troubleshoots and fixes network-related issues to ensure you stay connected to your gaming community without disruptions.
- Screen Display Challenges: Are you encountering display glitches or abnormalities? Trust Newtech to investigate and resolve firmware and hardware-related display issues for an optimal gaming experience with vibrant visuals.
- Hard Drive Problems: Facing difficulties with data transfers or experiencing file corruption? Our skilled technicians ensure smooth data handling and operational stability by addressing any hard drive issues efficiently.
- Power-Related Issues: Experiencing power-on troubles or unexpected game freezes? Let us conduct thorough hardware and software tests to diagnose and fix any power-related issues affecting your PS5’s performance.
- Controller Malfunctions: Is your PS5 controller acting erratically or not responding as it should? Our comprehensive examinations and fixes ensure uninterrupted gaming sessions with responsive controls.
At Newtech, we understand the importance of your gaming experience. Our dedicated specialists provide efficient and tailored solutions to restore your PS5 to its peak performance. Contact us today to get your console back on track and enjoy gaming without worries!
Cybersecurity Awareness Month: Training Strategies
Cybersecurity Awareness Month

Cybersecurity Awareness Month serves as a poignant reminder of the critical role employee training plays in fortifying a company’s defense strategy against cyber threats. Human error remains a significant factor in cyber incidents, underscoring the necessity for comprehensive training programs.
Understanding Human Vulnerabilities:
Cyber attackers often exploit common human vulnerabilities, such as susceptibility to phishing attacks, social engineering tactics, and a lack of awareness regarding security best practices. Recognizing these vulnerabilities is the first step toward mitigating risks.
Elements of Effective Training Programs:
A robust cybersecurity training program encompasses various key components. For instance, interactive modules, simulated phishing exercises, workshops, and ongoing education foster a culture of vigilance and equip employees with the knowledge and skills to identify and respond to potential threats.
Real-life Examples:
Numerous case studies illustrate the profound impact of successful employee training on thwarting cyber incidents. From foiling phishing attempts to preventing data breaches, well-trained employees serve as a formidable line of defense against cyber threats.
Measuring Training Effectiveness:
Assessing the effectiveness of training programs is essential for continuous improvement. Methods such as conducting simulated attacks, tracking changes in employee behavior, and monitoring incident response metrics provide valuable insights into the efficacy of training efforts.
Integration into Company Culture:
Embedding cybersecurity awareness into the organizational culture is paramount. Leadership support is instrumental in fostering a culture of security consciousness and ensuring ongoing commitment to training initiatives. By prioritizing cybersecurity education, companies can proactively reduce the risk of successful cyberattacks and cultivate a vigilant workforce.
In conclusion, investing in cybersecurity education for staff members is imperative for building a proactive defense against evolving cyber threats. By prioritizing employee training and integrating cybersecurity into the fabric of the organization, companies can significantly enhance their resilience to cyberattacks.
Ransomware Attacks: Understanding the Evolution
Cybersecurity Awareness Month

Evolution of Ransomware Attacks: Understanding Trends and Countermeasures
Ransomware attacks have evolved significantly over the years, becoming more sophisticated and pervasive. In this post, we’ll explore the current trends in ransomware attacks and effective countermeasures to mitigate their impact. From the historical progression of ransomware to recent trends such as double extortion and targeting critical infrastructure, we’ll delve into the key aspects of this evolving threat landscape. Additionally, we’ll analyze the impact of ransomware attacks on various industries and discuss the legal and ethical dilemmas surrounding ransom payments. Finally, we’ll conclude by emphasizing the importance of a multi-layered approach to cybersecurity in combating ransomware attacks effectively.
Ransomware Evolution: From Lockers to Encryption
Ransomware has evolved significantly over the years, progressing from early forms like locker ransomware to modern, complex strains such as file-encrypting ransomware.
Early Forms to Modern Strains: Understanding Ransomware Development
In the early days, locker ransomware simply restricted access to a device. Modern strains, however, encrypt files and demand ransom payments.
Emerging Trends in Ransomware Attacks: Double Extortion and Critical Infrastructure Targeting
Recent trends include a shift towards double extortion, where attackers not only encrypt data but also threaten to leak sensitive information unless additional ransom demands are met. Critical infrastructure has become a prime target for ransomware attacks, posing severe risks to essential services and public safety. Additionally, the rise of ransomware-as-a-service (RaaS) models has lowered the barrier to entry for cybercriminals.
Ransomware’s Toll on Various Sectors: Healthcare, Finance, and Government
Industries across the board have felt the impact of ransomware attacks. Healthcare institutions have faced disruptions to patient care, financial firms have grappled with data breaches and regulatory fines, and government agencies have encountered challenges in maintaining public trust and national security.
Combatting Ransomware Threats: Comprehensive Strategies for Defense
To combat ransomware threats effectively, organizations must implement a multi-faceted approach to cybersecurity. This includes regular data backups, network segmentation, robust endpoint protection solutions, comprehensive employee training, and well-defined incident response plans.
Paying the Price: Legal and Ethical Dilemmas of Ransomware Payments
The decision to pay ransom demands raises significant legal and ethical considerations. While paying the ransom may seem like a quick solution to regain access to encrypted data, it can also incentivize further attacks and contribute to the proliferation of ransomware. Organizations must carefully weigh the risks and implications of paying ransom demands, taking into account legal obligations, regulatory requirements, and ethical considerations.
In conclusion, ransomware attacks represent a persistent and evolving threat to organizations worldwide. By staying informed about the latest trends, implementing effective countermeasures, and adhering to legal and ethical guidelines, businesses can bolster their resilience against ransomware attacks and minimize potential damage.
Empowering Cybersecurity Simplification-Underdefense

In an era where digital threats loom large and security breaches are a constant concern for businesses of all sizes, UnderDefense introduces a game-changing solution: the MAXI Platform. Offering a holistic Security-as-a-Service (SECaaS) approach, this platform stands as the ultimate one-stop-shop for security and compliance needs.
Unlocking Cybersecurity Simplification for Enhanced Business Growth
The UnderDefense MAXI Platform is a product of extensive industry expertise. Consequently, it’s designed to empower organizations regardless of their size. Furthermore, it offers 24/7/365 end-to-end protection, detection, and response capabilities, making cybersecurity an effortless endeavor.
Ensuring Complete Security Measures: A Step-by-Step Guide
- Monitoring Excellence: Gain unparalleled visibility into your digital ecosystem. This ensures swift identification and response to any suspicious activity round the clock.
- Compliance Made Easy: Seamlessly integrate SIEM, Cloud, and EDR platforms. Additionally, utilize pre-built templates to adhere to the most stringent regulatory requirements without straining your resources.
- Automated Security: Enhance efficiency by automating routine security processes. This allows your team to focus on strategic initiatives while fortifying your defenses.
- Integration Flexibility: Irrespective of your existing digital infrastructure, the MAXI Platform smoothly integrates with over 45 legacy systems. Consequently, it eliminates the need for coding or redevelopment.
- Alert Optimization: Combat alert fatigue by filtering out false positives. Thus, ensuring that critical alerts are promptly addressed for a secure environment without overwhelming your team.
- Cost Optimization: Consolidate enterprise-wide protection under a single SECaaS solution. This enables a seamless setup without additional hires or hidden expenses. Transparent pricing ensures scalability without unexpected costs.
Leveraging the MAXI Platform: Your Competitive Security Edge
The brilliance of the UnderDefense MAXI Platform lies in its simplicity. By providing an all-encompassing solution, it eliminates the complexity of cybersecurity operations. Consequently, allowing organizations to focus on growth and innovation without compromising on security.
Tailored for All
Whether you’re a startup or an established enterprise, the MAXI Platform is tailored to meet your security needs. Offering a proactive, scalable, and affordable solution, it ensures that every business can fortify its defenses against modern cyber threats.
Future-Proof Security
Cyber threats evolve constantly. However, with the MAXI Platform, businesses gain a future-proof security strategy. The platform adapts and evolves alongside emerging threats. Hence, providing peace of mind and confidence in an ever-changing digital landscape.
Partnering for Success
UnderDefense doesn’t just offer a product; it’s a partner in your journey towards a secure future. With constant support, regular updates, and a commitment to staying ahead of the curve, it stands as a reliable ally in the fight against cyber threats.
The UnderDefense MAXI Platform represents a paradigm shift in the world of cybersecurity. By simplifying, unifying, and enhancing security operations, it enables organizations to navigate the digital realm with confidence and focus on what truly matters: growth, innovation, and success.
In a world where cyber threats are a constant battle, the MAXI Platform emerges as a beacon of comprehensive protection, ensuring that businesses thrive securely in the digital age.
Underdefence: Your Ultimate Cybersecurity Defender
In the current digital age, where businesses thrive on interconnected systems and data, the need for robust cybersecurity measures has never been more critical. Cyber threats loom large, posing significant risks to sensitive information and organizational integrity. Recognizing these challenges, UnderDefence emerges as a reliable partner, offering a comprehensive suite of cybersecurity services aimed at fortifying your defenses against evolving threats.
Unveiling UnderDefence's Holistic Cybersecurity Arsenal

Empower Your Team’s Cybersecurity with SecurityCoach from KnowBe4
Eliminating Mediators, Amplifying Expertise
By bypassing middlemen or outsourcers, UnderDefence positions itself as a cybersecurity heavyweight with a plethora of knowledge and expertise. Consequently, with this strategy, you can be sure that services will be provided directly and with excellent quality, maximizing efficiency and dependability in protecting your digital assets.
Managed Detection and Response: Uninterrupted Vigilance
Cyber threats are always changing and require constant observation. Therefore, UnderDefence continuously monitors your endpoints, providing you with a thorough picture of any potential security holes. Prompt action against potential backdoors stops hackers from gaining access to your system, thereby preventing them from attempting to undermine the integrity of your business.
Penetration Testing: Thwarting Vulnerabilities
Preventive actions are the cornerstone of a strong cybersecurity posture. Accordingly, UnderDefence uses manual penetration testing to examine your product source code and infrastructure in great detail. Consequently, the ensuing comprehensive analysis pinpoints weaknesses and provides tactical suggestions to strengthen security gaps efficiently.
Incident Response: Rapid Resolution, Swift Recovery
In cases of emergency, UnderDefence’s security squad is ready to go in the terrible case of a security breach. In cases involving encryption or data theft, prompt and accurate incident reaction is essential. Their knowledge not only fixes current problems but also strengthens your cybersecurity system to fend off intrusions in the future, guaranteeing a quick recovery and little interruption to business operations.
The UnderDefence Advantage: Unmatched Expertise, Proactive Solutions
In addition to offering services, UnderDefence provides peace of mind. They take a proactive approach to cybersecurity that goes beyond countering existing dangers. This proactive approach gives companies the ability to remain ahead of the curve in the cybersecurity space by strengthening defenses against new threats and constantly adapting.
Safeguarding Tomorrow’s Success Today
UnderDefence offers peace of mind in addition to services. They take a proactive approach to cybersecurity that goes beyond countering existing
Lenovo - Sustainability and Leadership

In a remarkable acknowledgment of its commitment to sustainability, Lenovo has been crowned a “Champion” vendor in the prestigious 2023 Canalys Global Sustainable Ecosystems Leadership Matrix. This recognition underscores Lenovo’s outstanding achievements in sustainability-focused partner programs and its robust organizational strategies.
A Pinnacle of Excellence
Lenovo stands among the top three industry vendors to attain the highest Champion status, a testament to its strong portfolio of sustainability solutions and unwavering dedication to decarbonization commitments. Moreover, this award reflects positive sentiments from the IT channel, highlighting Lenovo’s impactful sustainability initiatives.
A Legacy of Sustainability
Lenovo’s journey in sustainability dates back to 2008 when it published its first sustainability report. Since then, the company has consistently demonstrated leadership by being among the first to receive validation for its net-zero targets from the Science Based Targets initiative. This legacy of action underscores Lenovo’s ongoing dedication to environmental responsibility.
The Lenovo 360 Circle: Fostering Collaboration for a Sustainable Future
At the heart of Lenovo’s sustainability endeavors is the Lenovo 360 Circle. This global channel framework brings together partners to align on Environmental, Social, and Governance (ESG) objectives. Furthermore, the Lenovo 360 Circle serves as a platform for collaboration, encouraging partners to share best practices and collectively address sustainability challenges. Virginie Le Barbu, Lenovo’s Global Sustainability Director, expressed pride in leading the way with the Lenovo 360 Circle, emphasizing the importance of collaboration in driving sustainable impacts efficiently.
Sustainability as an Expectation
Pascal Bourguet, Lenovo’s Global Channel Chief, highlighted that sustainability is no longer an exception but an expectation. The Lenovo 360 global partner framework places sustainability solutions at the forefront of key business outcomes that partners can provide for their customers. Consequently, this approach reflects Lenovo’s commitment to integrating sustainability into the core of its business operations.
Beyond Recognition: Delivering Sustainable Services
In addition to its recognition in the Canalys Global Sustainable Ecosystems Leadership Matrix, Lenovo continues to innovate in sustainability services. For instance, the recently announced Reduced Carbon Transport service exemplifies Lenovo’s dedication to offering practical and impactful solutions for its customers.
Canalys Global Sustainable Ecosystems Leadership Matrix
The Canalys Global Sustainable Ecosystems Leadership Matrix is a comprehensive evaluation that considers 14 vendors based on their commitment and progress in driving sustainability in the partner ecosystem over the past 12 months. Lenovo’s recognition as a Champion reflects the company’s holistic approach. This approach combines ecosystem feedback, survey data, and independent assessments by Canalys analysts.
A Smarter, Inclusive, and Trustworthy Future
Lenovo, a US$62 billion revenue global technology powerhouse, is not just a leader in sustainability but also a force driving the advancement of ‘New IT’ technologies. With a bold vision to deliver smarter technology for all, Lenovo is building a more inclusive, trustworthy, and smarter future for everyone, everywhere.
For more details on Lenovo’s sustainability initiatives, including the Canalys Global Sustainable Ecosystems Leadership Matrix, and to explore the latest in Lenovo’s innovation, visit Lenovo’s official website.
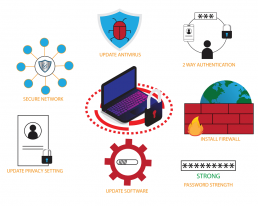
Cybersecurity Awareness Month - October

October is Cybersecurity Awareness Month
As we reach the middle of October, we find ourselves firmly in the heart of Cybersecurity Awareness Month. This is the perfect time to reflect on what we’ve learned and reiterate the importance of staying cyber-savvy. In a world where digital threats constantly evolve, staying informed and vigilant is paramount.
Mid-October Cybersecurity Checklist:
To ensure you’re on the right track in protecting your digital life, here’s a mid-October cybersecurity checklist:
- Review Your Passwords: Take some time to revisit your passwords. Are they strong and unique? Have you enabled 2FA wherever possible? If not, make the necessary changes.
- Check for Software Updates: Go through your devices and software applications. Make sure they’re all up to date. Cybercriminals often target vulnerabilities in outdated software.
- Phishing Awareness: Reiterate the importance of being cautious with emails, especially those from unknown senders. Double-check any suspicious links or attachments. Don’t let your guard down.
- Back Up Your Data: If you haven’t done so yet, set up a regular backup routine for your important data. This can be a lifesaver in the event of data loss due to cyberattacks.
- Stay Informed: Continue to educate yourself about emerging cybersecurity threats. Follow cybersecurity news, blogs, and resources to stay up-to-date.
- Family and Friends: Share your cybersecurity knowledge with friends and family. Many cybercrimes target less tech-savvy individuals, so help protect your loved ones too.
As we mark the midpoint of Cybersecurity Awareness Month, it’s a great time to take stock of your online security practices. By staying vigilant and following the best practices mentioned earlier in the month, you’re already on your way to a safer online experience.
Remember that cybersecurity is an ongoing effort. The threats keep evolving, and so should your defenses. Make it a habit to regularly update your knowledge and security measures. Your digital well-being is worth the effort, and you play a crucial role in creating a safer online environment.
Get Your Free Cybersecurity Awareness Month Resource Kit Now!
Cybersecurity Awareness Month

Cybersecurity Awareness Month!
Cybersecurity Awareness Month

Cybersecurity Awareness Month!
raising awareness about cybersecurity is crucial, especially during Cybersecurity Awareness Month. It’s a time when the spotlight shines on the importance of staying vigilant against cyber threats. Imagine malware lurking in an innocent-looking email, just waiting for someone to click. It’s like inviting the monsters under your bed into your network; spear phishing witches, ransomwolves, you name it!
But don’t panic just yet! While torches and pitchforks won’t solve this modern-day dilemma, fostering a resilient security culture within your organization can work wonders. That’s why we’re excited to share these invaluable resources from our partner KnowBe4, designed to fortify your cybersecurity defenses throughout October.
Here’s what’s in store for you:
- Access to a treasure trove of free resources, including KnowBe4’s most sought-after on-demand webinar and whitepaper.
- Handy planning tools, such as your Cybersecurity Awareness Month User Guide and Cybersecurity Awareness Weekly Planner.
- Brand new video content like “Security Culture and You,” along with eight more engaging modules available in multiple languages.
- Four informative security hints and tips newsletters, supplemented by additional security documents and awareness tips, all in multiple languages.
- Plus, dive into the realm of cyber-monsters with five character cards and posters, alongside other eye-catching assets in multiple languages.
In addition to these resources, it’s essential to highlight the significance of continuous education and training in cybersecurity. Threats are constantly evolving, and so should our defenses. Encouraging employees to stay informed about the latest trends in cyber attacks and best practices for preventing them can significantly enhance your organization’s security posture.
Furthermore, consider organizing interactive workshops or simulations to simulate real-world cyber threats and test employees’ responses. These hands-on experiences can help reinforce cybersecurity concepts and empower individuals to recognize and respond effectively to potential threats.
Remember, cybersecurity is everyone’s responsibility. By fostering a culture of security awareness and providing the necessary resources and support, we can collectively strengthen our defenses against cyber threats and protect our valuable assets.
Get Your Free Cybersecurity Awareness Month Resource Kit Now!
Get Your Kit!

Explore the Unknown - Password Guide
Tips For Password Security
The guidelines and steps for creating strong and secure passwords.
- Keep your passwords private – never share a password with anyone else
- Do not write down your passwords, use a password manager instead
- Use passwords of at least eight (8) characters or more (longer is better)
- Use a combination of upper case letters, lower case letters, numbers, and special characters (for example: !, @, &, %, +) in all passwords
- Avoid using people’s or pet’s names, or words found in the dictionary; it’s also best to avoid using key dates (birthdays, anniversaries, etc.)
- Substituting look-alike characters for letters or numbers is no longer sufficient (for example, Password” and “P@ssw0rd”)
- A strong password should look like a series of random characters
How To Create A Strong, Complex Password
Here’s a way to make a strong password that’s very hard to crack:
FOLLOW THESE STEPS
- Think of a phrase or sentence with at least eight words. It should be something easy for you to remember but hard for someone who knows you to guess. It could be a line from a favorite poem, story, movie, song lyric, or quotation you like.
Example:
I Want To Put A Dent In The Universe
- Remove all but the first letter of each word in your phrase.
IWTPADITU
- Replace several of the upper-case letters with lower case ones, at random.
iWtpADitU
- Now substitute a number for at least one of the letters. (Here, we’ve changed the capital “I” to the numeral 1).
iWtpAD1tU
- Finally, use special characters ( $, &, +, !, @) to replace a letter or two — preferably a letter that is repeated in the phrase. You can also add an extra character to the mix. (Here, we’ve replaced the “t” with “+”, and added an exclamation point at the end.)
iW+pAD1tU!
Why This Is Important ?
Traditional passwords can be cracked by hackers in less than a minute! Follow this guide to create passwords that would take centuries to crack.

Protect your home with APC. Power shortages? Invest in a UPS.
Protect your home with APC. Power shortages? Invest in a UPS.
Over the years, Schneider Electric has come out with durable, long lasting solutions, making them one of the most trusted companies worldwide in the realm of electronics. The German company owns APC, who specialize in products that power and safeguard the critical electronics at home that keep you and your family connected. The UPS allows you to protect your high speed internet connection with 24 /7 network access, ideal for storms and power outages. In case of a storm, APC filters electricity outputs in the event of an electric surge which could be caused by a lightening strike. This in turn prevents damage to all kind of devices from TV’s to consoles.
You are able to protect all of your data, including files stored on the cloud, streaming services and full access to send / receive emails during a power outage. APC solutions are proven to work harder, last longer and provide valuable protection to your home network. APC offer surge protectors, uninterruptible power supplies, that ensure you have optimal up time for your PC and home network. Whether it is for your home, home office and small business / server room and network closet / Data Centre and Facility. We are here to offer you solution.
As an official partner Newtech offer the full APC range, to select a UPS that is suited for your environment click here > https://www.apc.com/shop/mt/en/tools/ups_selector/
Once you select a model, please get in touch with our team of experts on ntsales@newtech.mt