7 Laptop Cleaning Tips for Peak Performance

Laptop Cleaning Tips for Maintenance and Longevity
Regularly Clean the Laptop Exterior
Laptop Cleaning Tips – It is essential for your laptop to be clean for its durability and optimal performance. Dust, dirt, and smudges can accumulate on your laptop’s surface and affect its functionality. We will provide you with seven practical tips to keep your laptop clean and well-maintained.
Keep the Keyboard Clean
The keyboard is prone to dirt and dust accumulation. Power down your laptop and use compressed air to dislodge any debris or crumbs nestled between the keys. For stubborn stains, a cotton swab dipped in isopropyl alcohol can help gently cleanse affected areas.
Utilize a Screen Cleaning Solution
Maintaining a spotless screen is crucial for optimal viewing. Power off your laptop and apply a small amount of screen cleaning solution to a microfiber cloth. Gently wipe the screen in circular motions, avoiding abrasive materials that could scratch its surface.
Ensure Adequate Ventilation
Proper airflow is essential for your laptop’s functionality and longevity. Regularly inspect and clear ventilation ports and fans of dust and debris using compressed air. Focus on areas around vents and fans to prevent overheating and sustain peak performance.
Avoid Food and Liquid Proximity
Protect your laptop from accidental spills and crumbs by establishing a strict no-food-and-drink policy while using it. This simple precaution can help preserve its cleanliness and safeguard against potential damage.
Optimal Storage and Transportation
Shield your laptop from scratches, dust, and impacts by storing it in a dedicated case or sleeve when not in use. During transport, employ a padded bag or backpack designed for laptops to mitigate the risk of damage.
Implement Routine Software Maintenance
Elevate your maintenance routine beyond physical cleaning by ensuring your software is up to date. Regularly update your operating system and antivirus software, remove unnecessary programs and files, and run disk cleanup and defragmentation utilities to optimize performance and security.
By adhering to these laptop cleaning tips, you can uphold the cleanliness, functionality, and longevity of your device. From meticulous exterior care to diligent software maintenance, these practices are essential for preserving your laptop’s performance for years to come.
https://newtech.mt/service-centers-repairs/
Authorized Service Centre for Lenovo, Acer, and MSI

Providing Reliable Service:
Authorized Service Center for Lenovo, Acer, and MSI
In today’s world, having access to reliable and efficient service centers is crucial for customers who encounter issues with their electronic devices. We are proud to announce that our service center has earned the prestigious status of being an authorized service center for three leading technology brands: Lenovo, Acer, and MSI. This achievement reflects our commitment to providing high-quality repair and maintenance services to our valued customers.
Expertise and Accreditation
Becoming an authorized service center involves strict requirements and demonstrating expertise in handling products from these renowned brands. Firstly, we have gone through a strict evaluation process, ensuring that we have the necessary technical knowledge, infrastructure, and genuine spare parts to offer quality service.
Moreover, our team of highly trained technicians possesses in-depth knowledge about Lenovo, Acer, and MSI devices. Whether it’s a malfunctioning laptop, a tablet with a cracked screen, or a gaming PC in need of an upgrade, we have the expertise to diagnose and resolve issues efficiently. Our technicians stay up to date with the latest product developments, furthermore, troubleshooting techniques, and repair methodologies through continuous training provided by the manufacturers.
Skilled Technicians and Continuous Training
Our team of highly trained technicians possesses in-depth knowledge about Lenovo, Acer, and MSI devices. Whether it’s a malfunctioning laptop, a tablet with a cracked screen, or a gaming PC in need of an upgrade, we have the expertise to diagnose and resolve issues efficiently. Our technicians stay up to date with the latest product developments, troubleshooting techniques, and repair methodologies through continuous training provided by the manufacturers.
Access to Official Tools and Genuine Parts
Additionally, as an authorized service center, we have access to official repair tools, diagnostic software, and genuine parts provided directly by Lenovo, Acer, and MSI. This ensures that we can perform repairs and replacements using original components, maintaining the integrity and performance of the devices.
Warranty Support and Customer Satisfaction
Customers who bring their Lenovo, Acer, and MSI products to our service center can enjoy the benefits of warranty support. We handle warranty claims efficiently, furthermore, we stick to the manufacturers’ guidelines and processes. Consequently, with our authorized status, customers can have peace of mind knowing that their devices are being serviced by professionals who understand the intricacies of the products.
Transparent Service and Trust
Our focus is customer satisfaction. Therefore, we strive to provide a smooth experience to our customers, ensuring prompt service, clear communication, and transparent pricing. By offering authorized service, we instill trust in our customers, thus assuring them that their devices are in capable hands and will be repaired to the highest standards.
Exceptional Service for Lenovo, Acer, and MSI Customers
As an authorized service center for Lenovo, Acer, and MSI, we are committed to delivering reliable, efficient, and professional repair services. Our expertise gives us access to official tools and genuine parts, and our loyalty to warranty support guidelines set us apart from unauthorized service providers.
We invite Lenovo, Acer, and MSI customers to experience our exceptional service and trust us with their valuable devices.
Explore the Unknown - Password Guide
Tips For Password Security
The guidelines and steps for creating strong and secure passwords.
- Keep your passwords private – never share a password with anyone else
- Do not write down your passwords, use a password manager instead
- Use passwords of at least eight (8) characters or more (longer is better)
- Use a combination of upper case letters, lower case letters, numbers, and special characters (for example: !, @, &, %, +) in all passwords
- Avoid using people’s or pet’s names, or words found in the dictionary; it’s also best to avoid using key dates (birthdays, anniversaries, etc.)
- Substituting look-alike characters for letters or numbers is no longer sufficient (for example, Password” and “P@ssw0rd”)
- A strong password should look like a series of random characters
How To Create A Strong, Complex Password
Here’s a way to make a strong password that’s very hard to crack:
FOLLOW THESE STEPS
- Think of a phrase or sentence with at least eight words. It should be something easy for you to remember but hard for someone who knows you to guess. It could be a line from a favorite poem, story, movie, song lyric, or quotation you like.
Example:
I Want To Put A Dent In The Universe
- Remove all but the first letter of each word in your phrase.
IWTPADITU
- Replace several of the upper-case letters with lower case ones, at random.
iWtpADitU
- Now substitute a number for at least one of the letters. (Here, we’ve changed the capital “I” to the numeral 1).
iWtpAD1tU
- Finally, use special characters ( $, &, +, !, @) to replace a letter or two — preferably a letter that is repeated in the phrase. You can also add an extra character to the mix. (Here, we’ve replaced the “t” with “+”, and added an exclamation point at the end.)
iW+pAD1tU!
Why This Is Important ?
Traditional passwords can be cracked by hackers in less than a minute! Follow this guide to create passwords that would take centuries to crack.

Email Vigilance Checklist: Safeguarding Your Inbox
Email Vigilance Checklist: Safeguarding Your Inbox
In today’s digital age, email has become an indispensable tool for communication in both personal and professional spheres. However, with the convenience of email also comes the risk of cyber threats such as phishing, malware, and spoofing. To protect yourself and your organization from these dangers, it’s crucial to adopt robust email security practices. Here are some essential tips to help you safeguard your inbox:
Validate Sender Information:
Always scrutinize the ‘from’ field of an email to verify the sender’s identity. Keep in mind that malicious actors can easily spoof email addresses to deceive recipients. If an email seems suspicious or unexpected, double-check the sender’s details before taking any further action.
Exercise Caution with Attachments:
Be cautious when opening email attachments, particularly those with executable file extensions such as ‘.exe’. A general rule of thumb is to avoid opening attachments from unknown or untrusted sources. Additionally, be wary of files with double extensions (e.g., ‘safe.txt.exe’), as they could contain harmful malware.
Report Suspicious Activity:
If you receive an email that raises suspicions or appears to be a phishing attempt, report it immediately to your organization’s IT help desk or security team. Prompt reporting can help prevent potential security breaches and protect other users within your organization.
Verify Hyperlinks:
Before clicking on any hyperlinks embedded in an email, hover your mouse cursor over the link to preview the URL. Watch out for discrepancies between the displayed URL and the actual destination. Be especially cautious of hyperlinks that lead to unfamiliar or suspicious websites, as they could be phishing sites designed to steal your personal information.
Stay Vigilant Against Domain Spoofing:
Cybercriminals often use domain spoofing techniques to create fraudulent websites that mimic legitimate ones. Pay close attention to the domain name in email links and be wary of subtle variations or misspellings. For example, ‘www.bankofarnerica.com‘ may appear similar to the legitimate ‘www.bankofamerica.com‘, but it could lead to a malicious site.
By adhering to these email security best practices, you can significantly reduce the risk of falling victim to cyber threats and protect your sensitive information. Remember, maintaining a vigilant and cautious approach to email communication is key to safeguarding both your personal and professional digital assets.
If you have any further questions or concerns about email security, don’t hesitate to reach out to your organization’s IT support team for assistance. Stay safe, stay secure!

Red Flags - Stay Alert and Stay Safe
Red Flags – Social Engineering
Identify Red Flags in an Email
Identifying red flags in an email is crucial to stay alert and stay safe from social engineering attacks. Here’s a breakdown of what to look out for:
Stay Alert: Red Flags From the Sender:
- First and foremost, check if the sender’s email address is unfamiliar or unrelated to your usual contacts.
- Additionally, scrutinize whether the email is from someone outside your organization, not related to your job responsibilities.
- Equally important is to assess if the email is from someone inside your organization, but the content is unusual or out of character.
- Furthermore, watch out for suspicious sender email domains, like “micorsoft support.com.”
- Moreover, consider if there’s a lack of personal acquaintance or endorsement from someone you trust.
- Take note if there’s no prior business relationship or communication history with the sender.
- Lastly, be wary of unexpected or unusual content, especially with embedded hyperlinks or attachments.
Stay Safe: Spotting Suspicious Hyperlinks:
- It’s important to mention that hovering over a hyperlink reveals a different destination URL, a significant red flag.
- Another key point is that emails with only long hyperlinks and no further context or content are suspicious.
- Additionally, be cautious of misspelled hyperlinks mimicking known websites, such as “www.bankofarnerica.com.”
Stay Vigilant: Identifying Unusual Recipients and Attachments:
- Consider whether you’ve been cc’d on an email to unfamiliar recipients.
- Additionally, be cautious of emails sent to an unusual mix of people, such as random groups or unrelated addresses.
- Look out for unexpected or nonsensical attachments, especially from senders who don’t typically send such files.
- Also, be cautious of attachments with potentially dangerous file types, with .txt files being the only inherently safe type.
Stay Aware: Timing, Subject Lines, and Content:
- It’s worth noting if emails are received at unusual times, especially outside regular business hours.
- Take note of irrelevant subject lines or subject lines that don’t match the email content.
- Similarly, be cautious of emails that appear as replies to unrequested or unsent messages.
- Pay attention to requests to click on links or open attachments under the threat of negative consequences or with promises of gain.
- Also, watch out for unusual or poor grammar and spelling errors in the email.
- Additionally, consider whether there are illogical or suspicious requests to click on links or open attachments.
- Trust your instincts if you sense discomfort or suspicion regarding the email’s content.
- Lastly, be cautious of emails requesting viewing of compromising or embarrassing images.
By being vigilant and attentive to these red flags, you can protect yourself and your organization from falling victim to social engineering attacks.
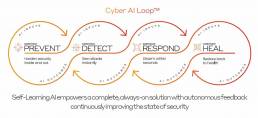
Enhancing Cybersecurity - Continuous Cyber AI Loop
Darktrace’s technology vision is a continuous, Cyber AI Loop™, where each capability autonomously feeds back into the system as a whole, continuously improving the state of cyber security.
Improving Awareness and Decision-Making
From the attacker's perspective, Darktrace PREVENT provides vital insights to defenders. Consequently, it enables them to identify existing devices that are externally facing or part of a critical attack path, enhancing their overall awareness of the environment.
Moreover, users benefit from contextual information about external facing assets and critical attack paths via tags in the DETECT and RESPOND user interface. This enables better decisions, quicker triage, and facilitates further modeling using this new information. For example, if PREVENT identifies a web server on a critical attack path, relevant entities receive tags in DETECT, providing crucial knowledge for detection modeling and AI Analyst investigations.
Incorporating Industry Standards for Faster Understanding
Darktrace incorporates the MITRE ATTACK Framework across the loop. Additionally, it tags devices identified by Darktrace PREVENT as sitting on a critical attack path with MITRE techniques corresponding to the inbound and outbound parts of the attack path. This provides automatic mapping to an industry-standard attack framework for auditing, compliance, and faster understanding of all components of the attack.
Richer AI Analyst Investigations
AI Analyst investigations become richer as they enrich existing investigations with malicious hostnames retrieved from PREVENT/ASM. Consequently, this indicates they are more likely to be suspicious and potentially part of an incident.
Heightening Email Security
Darktrace PREVENT/Attack Surface Management informs Darktrace/Email of potential threats, such as domain spoofing. This action heightens sensitivity around these assets and takes action when these spoof domains are used for malicious purposes. Hence, this leads to more accurate decision-making in the email realm, reducing analysis time for individual emails.
Consolidating Insights for Better Response
Assets confirmed as malicious by Darktrace PREVENT/Attack Surface Management automatically become ‘Watched Domains’ in Darktrace/Network. This enhancement enables security teams to consolidate insights from inside the business and externally on the attack surface in a single pane of glass, improving their ability to respond effectively.
Darktrace Prevent- Cyber Resilience Reinforcement
Darktrace Prevent
Hardens security Proactively
Identifies and prioritizes risks
Emulates attacks to test vulnerabilities
Helps organizations meet NIST and other regulations
Reinforcing Cyber Resilience with Darktrace PREVENT
In today’s rapidly evolving cybersecurity landscape, fortifying your defenses is paramount to safeguarding your organization against emerging threats. Darktrace PREVENT offers a proactive approach to cybersecurity, empowering organizations to anticipate and thwart future attacks.
Enhanced Visibility with Darktrace PREVENT/ASM
Darktrace PREVENT/ASM provides unparalleled visibility into your organization’s external exposure, enabling proactive risk identification and mitigation before an attack occurs. By continuously monitoring the external attack surface, PREVENT/ASM assesses all assets for risks, vulnerabilities, and threats, helping you stay one step ahead of potential attackers.

Darktrace PREVENT / Attack Surface Management™
Enter Darktrace PREVENT, an interconnected suite of AI products designed to provide proactive cybersecurity, helping organizations anticipate future cyber-attacks. This product family empowers CISOs and security staff to function as an AI-powered Red Team, simulating attacks, identifying critical assets, testing vulnerability pathways, and fortifying defenses to thwart attackers from compromising vital systems and data.
One component of Darktrace PREVENT is Attack Surface Management™ (ASM), which offers unparalleled visibility into the organization’s external exposure, enabling the security team to proactively identify risks before an attack occurs. ASM continuously monitors the external attack surface, assessing all assets for risks, high-impact vulnerabilities, and external threats. It is instrumental in revealing shadow IT, supply chain risks, potential phishing domains, vulnerabilities, misconfigurations, and risks associated with mergers and acquisitions. Additionally, ASM communicates its findings to Darktrace DETECT + RESPOND, enhancing sensitivity around critical chokepoints.
Darktrace PREVENT / End-to-End™
Attack Path Modeling
Maps the most relevant and impactful attack paths through your organization in real time.
Pentest Augmentation
Tests all potential attack pathways around the clock.
Breach & Attack Emulation
Deploys harmless “attacks” that emulate malware, phishing, spoofing, and other common threats.
Security & Awerness Training
Identifies users who are exposed or vulnerable to phishing, allowing IT teams to tailor training based on real-world data.
Cyber Risk Prioritization
Continuously updates its findings to show you which areas of focus would reduce risk to the greatest extent.

Darktrace Solutions Feed Back into the Cyber AI Loop™
Darktrace PREVENT forms part of Darktrace’s Cyber AI Loop, which orchestrates a set of dynamically related cyberthreat capabilities. Combined with Darktrace DETECT™ + RESPOND™, Darktrace PREVENT autonomously implements countermeasures to harden your defenses around critical vulnerabilities and attack paths.
Darktrace Cyber AI Loop why Darktrace?
Why Darktrace?
Reduces the risk by prioritizing vulnerabilities and hardening systems
Gain instant visibility of previously unknown and unpredictable attacks
Minimize disruption with a targeted, autonomous response to cyber-attacks
Augment and empower security teams with always-on, AI-driven capabilities
The only Comprehensive, Always-on, End-to-End, Cyber Security

The groundbreaking Darktrace Cyber AI Loop introduces an integrated suite of cybersecurity solutions that continuously fortifies your defenses. This revolutionary system comprises four AI-driven product families – Darktrace PREVENT™, Darktrace DETECT™, Darktrace RESPONDTM, and Darktrace HEAL™ – which collaborate seamlessly across your organization.
By leveraging Self-Learning AI technology, Darktrace tailors its solutions to your specific organization, illuminating and neutralizing previously unseen threats. This article explores how Darktrace’s AI-powered approach revolutionizes cybersecurity, offering unparalleled protection against evolving cyber threats.
Darktrace Detect & Respond
Autonomous Response: Disarm Attacks in Seconds
Cyber AI Analyst
Uplift and Augment Your Security Team with AI Investigations
Darktrace Prevent
Hardening Security and Reducing Risk
Darktrace DETECT + RESPOND leverages deep organizational understanding to tailor responses to specific threats, neutralizing malicious activity without disrupting normal business operations. This approach contrasts with automated solutions reliant on predefined playbooks, which may lead to imprecise, heavy-handed actions.
Darktrace’s Cyber AI Analyst streamlines threat investigation by continuously assessing security threats, identifying top priorities, and synthesizing attack context into natural language reports. This reduces time-to-understanding and time-to-response, enabling security teams to focus their expertise where it’s most needed.
Darktrace PREVENT empowers CISOs and security teams to transition from reactive to proactive security measures, prioritizing threats, optimizing defenses, and reducing overall cyber risk.
KnowBe4 Security Awerness Training
KnowBe4 Security Awerness Training
KnowBe4 Security Awareness Training, the largest complete Security Awareness Training and Simulated Phishing platform in the world, has more than 50,000 users. With this platform, you now have a comprehensive solution to better manage IT security issues, including social engineering, spear phishing, and ransomware assaults.
Training and Testing Features:
KnowBe4 offers self-service enrollment. Additionally, it provides world-class, user-friendly new-school security awareness training. Furthermore, it offers pre-and post-training phishing security tests to reveal the proportion of end users that are Phish-prone. Moreover, KnowBe4’s very efficient, regular, random Phishing Security Tests offer several corrective measures.
Assessment and Evaluation:
Utilize KnowBe4 Assessments to evaluate your users’ security awareness skills and the broader security culture of your company. These evaluations assist you in modifying training to meet knowledge gaps and weaknesses. Additionally, they help in tracking the effects of your security awareness training program on enhancing users’ security awareness knowledge and attitudes over time.
Benchmarking and Comparison:
You can contrast your organization’s security awareness proficiency results with those of other businesses in your sector using the tools of the Security Awareness Proficiency Assessment and Security Culture Survey. Examine your organization’s performance in relation to the seven security knowledge areas and the seven dimensions of security culture using the results of your baseline assessment and survey. Also, keep track of how well your organization is doing over time.
User Experience Enhancements:
With the updated end-user security awareness training interface, your users will enjoy a brand-new learning environment that makes learning enjoyable and engaging. Additionally, you can provide your users with 24/7 access to assigned training via the KnowBe4 Learner App. This makes it simple for them to learn whenever and wherever they want. Moreover, the localized training interface for KnowBe4 is offered in a variety of languages, allowing your users to select the one they feel most at ease using for an immersive training experience.
Customization Options:
If you want to add custom training or other corporate training materials to the KnowBe4 security awareness training materials, you can now do so. You can manage both your own SCORM-compliant training and video materials in one location, together with the KnowBe4 ModStore training material.
Risk Detection and Reporting:
You may begin to detect risk at the user, group, and organizational levels with the new Virtual Risk Officer and Advanced Reporting tools. These tools will assist you in making data-driven decisions regarding your security awareness plan. Additionally, you may assess the success of your security awareness training program by looking at next-level reporting for simulated phishing and security awareness training campaigns.
Automated Program Implementation:
When it comes to developing a security awareness program that will work for their firm, many IT professionals are unsure about where to begin. With the help of our Automated Security Awareness Program, we have eliminated all the uncertainty. If you want to implement all the procedures to establish a comprehensive security awareness training program for your firm quickly, ASAP enables you to create a bespoke curriculum for it.
Develop Your Users
The greatest collection of security awareness training materials available anywhere in the globe, including newsletters, interactive modules, movies, games, and posters. automated reminder emails for training campaigns.
Phish Your Users
Thousands of templates with limitless use and best-in-class, fully automated simulations of phishing assaults.
See The Results
Management-ready, enterprise-strength reporting with statistics and graphs for security awareness training and phishing. Show the fantastic ROI!
Cybersecurity Trends to watch out for in 2023
Cybersecurity Trends to Watch Out For in 2023
Emerging Cybersecurity Trends 2023:
With the digital revolution, corporations, organizations, and even governments are turning to computerized systems to conduct their daily operations. As a result, cybersecurity has become a top priority to protect data from various online threats and any unauthorized access. As news of data breaches, ransomware, and hacking becomes the norm, it follows that there will be a similar shift in cybersecurity trends as a result of ongoing technological advancement.
The top cybersecurity trends for 2023:
1. An increase in automotive hacking
Today’s vehicles are loaded with automated software that enables smooth connectivity for drivers in areas like airbags, cruise control, door locks, and advanced driver aid systems. These vehicles use Bluetooth and WiFi to connect, which exposes them to a number of security flaws or hacker threats. With more automated vehicles on the road in 2023, it’s anticipated that attempts to take control of them or listen in on conversations will increase. Autonomous or self-driving vehicles use an even more complicated process that demands stringent cybersecurity precautions.
2. Artificial intelligence’s potential (AI)
With the introduction of AI into all commercial sectors, this technology combined with machine learning has significantly altered cyber security. The development of automated security systems, natural language processing, facial detection, and autonomous threat detection have all benefited greatly from AI. However, it also creates clever malware and attacks that get through the most recent data security mechanisms. Threat detection systems with AI capabilities can anticipate new assaults and immediately alert administrators to any data breach.
3. The New Target is Mobile
Our emails, chats, financial transactions, and images all pose greater risks to people. The malware or virus that affects smartphones may be the focus of 2023’s cybersecurity developments.
4. Additionally Potentially Vulnerable is Cloud
To protect the data from leaks, security procedures must be regularly evaluated and upgraded as more businesses establish themselves in the cloud. Although cloud programs like those from Google and Microsoft still have strong security measures in place, it’s the user end that often leads to mistakes, malicious software, and phishing scams.
5. Data breaches: key objective
Organizations all over the world will continue to prioritize data. Protecting digital data is now the main objective, whether for an individual or a business. Any tiny defect or weakness in your computer’s software or browser could allow hackers access to your sensitive data. From May 25th, 2018, new, strict regulations known as the General Data Protection Regulation (GDPR) went into effect, providing individuals in the European Union with data protection and privacy (EU). Similar to this, starting on January 1st, 2020, the California Consumer Privacy Act (CCPA) was implemented to protect consumer rights in the state of California.
6. The New Era of Technology and Risks in the IoT with 5G Network
A new age of interconnectivity with the Internet of Things will be possible with the arrival and expansion of 5G networks (IoT). See What the Internet of Things (IoT) Is and Why It Matters for further information. Multiple devices communicating with one another exposes them to threats from the outside world, assaults, or unidentified software bugs. Even Chrome, the most popular browser in the world sponsored by Google, was discovered to contain significant problems. The 5G architecture is still relatively new in the market, therefore it will take a lot of investigation to uncover vulnerabilities that will allow the system to be protected from outside assault. Every phase of the 5G network could result in a slew of network attacks that we might not be prepared for.
7. Integration and Automation
Automation must be integrated to provide more sophisticated control over the data because data size is increasing daily. Automation is more vital than ever because of the pressure placed on experts and engineers by today’s frantic job demands to provide rapid and effective solutions. To create software that is more safe in every way, security metrics are incorporated into the agile development process. Due to the difficulty in protecting large and sophisticated web applications, automation and cyber security are significant concepts in the software development process.
8. Specific ransomware
Targeted ransomware is another significant cybersecurity development that we are unable to ignore. Industries, particularly those in industrialized countries, rely largely on particular software to carry out their daily operations. The Wanna Cry attack on National Health Service hospitals in England and Scotland corrupted more than 70,000 medical devices. These ransomware targets are highly targeted. Even though ransomware typically threatens to make the victim’s data public unless a ransom is paid, it can also harm very large organizations or entire countries.
9. Cyberwarfare Sponsored by the TaState
The competition between the western and eastern powers to establish superiority won’t be stopped. Despite the attacks being rare, the conflict between the US and Iran or Chinese hackers frequently makes headlines around the world and has a big impact on events like elections. Additionally, with more than 70 elections expected to be held this year, criminal activity will increase at this time. Political and business secrets, as well as high-profile data breaches, are predicted to dominate cybersecurity themes in 2023.
10. Internal Threats
One of the main causes of the data breach is still human mistake. Millions of stolen data can bring down a whole corporation on any bad day or purposeful loophole. 34 percent of all attacks were either directly or indirectly carried out by workers, according to a report by Verizon on a data breach that provides strategic insights on cybersecurity trends. Therefore, be sure to raise awareness about data security within the facility.
https://newtech.mt/cybersecurity/




