Darktrace Cyber AI Loop why Darktrace?
Why Darktrace?
Reduces the risk by prioritizing vulnerabilities and hardening systems
Gain instant visibility of previously unknown and unpredictable attacks
Minimize disruption with a targeted, autonomous response to cyber-attacks
Augment and empower security teams with always-on, AI-driven capabilities
The only Comprehensive, Always-on, End-to-End, Cyber Security
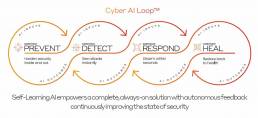
The groundbreaking Darktrace Cyber AI Loop introduces an integrated suite of cybersecurity solutions that continuously fortifies your defenses. This revolutionary system comprises four AI-driven product families – Darktrace PREVENT™, Darktrace DETECT™, Darktrace RESPONDTM, and Darktrace HEAL™ – which collaborate seamlessly across your organization.
By leveraging Self-Learning AI technology, Darktrace tailors its solutions to your specific organization, illuminating and neutralizing previously unseen threats. This article explores how Darktrace’s AI-powered approach revolutionizes cybersecurity, offering unparalleled protection against evolving cyber threats.
Darktrace Detect & Respond
Autonomous Response: Disarm Attacks in Seconds
Cyber AI Analyst
Uplift and Augment Your Security Team with AI Investigations
Darktrace Prevent
Hardening Security and Reducing Risk
Darktrace DETECT + RESPOND leverages deep organizational understanding to tailor responses to specific threats, neutralizing malicious activity without disrupting normal business operations. This approach contrasts with automated solutions reliant on predefined playbooks, which may lead to imprecise, heavy-handed actions.
Darktrace’s Cyber AI Analyst streamlines threat investigation by continuously assessing security threats, identifying top priorities, and synthesizing attack context into natural language reports. This reduces time-to-understanding and time-to-response, enabling security teams to focus their expertise where it’s most needed.
Darktrace PREVENT empowers CISOs and security teams to transition from reactive to proactive security measures, prioritizing threats, optimizing defenses, and reducing overall cyber risk.
KnowBe4 Security Awerness Training
KnowBe4 Security Awerness Training
KnowBe4 Security Awareness Training, the largest complete Security Awareness Training and Simulated Phishing platform in the world, has more than 50,000 users. With this platform, you now have a comprehensive solution to better manage IT security issues, including social engineering, spear phishing, and ransomware assaults.
Training and Testing Features:
KnowBe4 offers self-service enrollment. Additionally, it provides world-class, user-friendly new-school security awareness training. Furthermore, it offers pre-and post-training phishing security tests to reveal the proportion of end users that are Phish-prone. Moreover, KnowBe4’s very efficient, regular, random Phishing Security Tests offer several corrective measures.
Assessment and Evaluation:
Utilize KnowBe4 Assessments to evaluate your users’ security awareness skills and the broader security culture of your company. These evaluations assist you in modifying training to meet knowledge gaps and weaknesses. Additionally, they help in tracking the effects of your security awareness training program on enhancing users’ security awareness knowledge and attitudes over time.
Benchmarking and Comparison:
You can contrast your organization’s security awareness proficiency results with those of other businesses in your sector using the tools of the Security Awareness Proficiency Assessment and Security Culture Survey. Examine your organization’s performance in relation to the seven security knowledge areas and the seven dimensions of security culture using the results of your baseline assessment and survey. Also, keep track of how well your organization is doing over time.
User Experience Enhancements:
With the updated end-user security awareness training interface, your users will enjoy a brand-new learning environment that makes learning enjoyable and engaging. Additionally, you can provide your users with 24/7 access to assigned training via the KnowBe4 Learner App. This makes it simple for them to learn whenever and wherever they want. Moreover, the localized training interface for KnowBe4 is offered in a variety of languages, allowing your users to select the one they feel most at ease using for an immersive training experience.
Customization Options:
If you want to add custom training or other corporate training materials to the KnowBe4 security awareness training materials, you can now do so. You can manage both your own SCORM-compliant training and video materials in one location, together with the KnowBe4 ModStore training material.
Risk Detection and Reporting:
You may begin to detect risk at the user, group, and organizational levels with the new Virtual Risk Officer and Advanced Reporting tools. These tools will assist you in making data-driven decisions regarding your security awareness plan. Additionally, you may assess the success of your security awareness training program by looking at next-level reporting for simulated phishing and security awareness training campaigns.
Automated Program Implementation:
When it comes to developing a security awareness program that will work for their firm, many IT professionals are unsure about where to begin. With the help of our Automated Security Awareness Program, we have eliminated all the uncertainty. If you want to implement all the procedures to establish a comprehensive security awareness training program for your firm quickly, ASAP enables you to create a bespoke curriculum for it.
Develop Your Users
The greatest collection of security awareness training materials available anywhere in the globe, including newsletters, interactive modules, movies, games, and posters. automated reminder emails for training campaigns.
Phish Your Users
Thousands of templates with limitless use and best-in-class, fully automated simulations of phishing assaults.
See The Results
Management-ready, enterprise-strength reporting with statistics and graphs for security awareness training and phishing. Show the fantastic ROI!
Cybersecurity Trends to watch out for in 2023
Cybersecurity Trends to Watch Out For in 2023
Emerging Cybersecurity Trends 2023:
With the digital revolution, corporations, organizations, and even governments are turning to computerized systems to conduct their daily operations. As a result, cybersecurity has become a top priority to protect data from various online threats and any unauthorized access. As news of data breaches, ransomware, and hacking becomes the norm, it follows that there will be a similar shift in cybersecurity trends as a result of ongoing technological advancement.
The top cybersecurity trends for 2023:
1. An increase in automotive hacking
Today’s vehicles are loaded with automated software that enables smooth connectivity for drivers in areas like airbags, cruise control, door locks, and advanced driver aid systems. These vehicles use Bluetooth and WiFi to connect, which exposes them to a number of security flaws or hacker threats. With more automated vehicles on the road in 2023, it’s anticipated that attempts to take control of them or listen in on conversations will increase. Autonomous or self-driving vehicles use an even more complicated process that demands stringent cybersecurity precautions.
2. Artificial intelligence’s potential (AI)
With the introduction of AI into all commercial sectors, this technology combined with machine learning has significantly altered cyber security. The development of automated security systems, natural language processing, facial detection, and autonomous threat detection have all benefited greatly from AI. However, it also creates clever malware and attacks that get through the most recent data security mechanisms. Threat detection systems with AI capabilities can anticipate new assaults and immediately alert administrators to any data breach.
3. The New Target is Mobile
Our emails, chats, financial transactions, and images all pose greater risks to people. The malware or virus that affects smartphones may be the focus of 2023’s cybersecurity developments.
4. Additionally Potentially Vulnerable is Cloud
To protect the data from leaks, security procedures must be regularly evaluated and upgraded as more businesses establish themselves in the cloud. Although cloud programs like those from Google and Microsoft still have strong security measures in place, it’s the user end that often leads to mistakes, malicious software, and phishing scams.
5. Data breaches: key objective
Organizations all over the world will continue to prioritize data. Protecting digital data is now the main objective, whether for an individual or a business. Any tiny defect or weakness in your computer’s software or browser could allow hackers access to your sensitive data. From May 25th, 2018, new, strict regulations known as the General Data Protection Regulation (GDPR) went into effect, providing individuals in the European Union with data protection and privacy (EU). Similar to this, starting on January 1st, 2020, the California Consumer Privacy Act (CCPA) was implemented to protect consumer rights in the state of California.
6. The New Era of Technology and Risks in the IoT with 5G Network
A new age of interconnectivity with the Internet of Things will be possible with the arrival and expansion of 5G networks (IoT). See What the Internet of Things (IoT) Is and Why It Matters for further information. Multiple devices communicating with one another exposes them to threats from the outside world, assaults, or unidentified software bugs. Even Chrome, the most popular browser in the world sponsored by Google, was discovered to contain significant problems. The 5G architecture is still relatively new in the market, therefore it will take a lot of investigation to uncover vulnerabilities that will allow the system to be protected from outside assault. Every phase of the 5G network could result in a slew of network attacks that we might not be prepared for.
7. Integration and Automation
Automation must be integrated to provide more sophisticated control over the data because data size is increasing daily. Automation is more vital than ever because of the pressure placed on experts and engineers by today’s frantic job demands to provide rapid and effective solutions. To create software that is more safe in every way, security metrics are incorporated into the agile development process. Due to the difficulty in protecting large and sophisticated web applications, automation and cyber security are significant concepts in the software development process.
8. Specific ransomware
Targeted ransomware is another significant cybersecurity development that we are unable to ignore. Industries, particularly those in industrialized countries, rely largely on particular software to carry out their daily operations. The Wanna Cry attack on National Health Service hospitals in England and Scotland corrupted more than 70,000 medical devices. These ransomware targets are highly targeted. Even though ransomware typically threatens to make the victim’s data public unless a ransom is paid, it can also harm very large organizations or entire countries.
9. Cyberwarfare Sponsored by the TaState
The competition between the western and eastern powers to establish superiority won’t be stopped. Despite the attacks being rare, the conflict between the US and Iran or Chinese hackers frequently makes headlines around the world and has a big impact on events like elections. Additionally, with more than 70 elections expected to be held this year, criminal activity will increase at this time. Political and business secrets, as well as high-profile data breaches, are predicted to dominate cybersecurity themes in 2023.
10. Internal Threats
One of the main causes of the data breach is still human mistake. Millions of stolen data can bring down a whole corporation on any bad day or purposeful loophole. 34 percent of all attacks were either directly or indirectly carried out by workers, according to a report by Verizon on a data breach that provides strategic insights on cybersecurity trends. Therefore, be sure to raise awareness about data security within the facility.
https://newtech.mt/cybersecurity/
AI threat detection that ‘understands you’ critical to thwarting attacks
Detection is crucial in cybersecurity, but it’s just one aspect of today’s complex landscape. Threat actors leverage open-source code, AI, and MFA as potent weapons, necessitating continuous and adaptive security measures across an organization’s digital ecosystem.
Toby Lewis, from Darktrace, emphasizes AI’s role in threat detection. This technology comprehends organizational behavior and establishes a baseline of normalcy. It discerns known and unknown threats, making real-time decisions to mitigate risks effectively.
Lewis highlights the relentless pace and complexity of cyberattacks, necessitating a proactive defense strategy. Despite efforts, it’s challenging to monitor every digital aspect simultaneously. With cloud computing, SaaS, and IoT, the attack surface expands, leaving enterprises vulnerable to diverse threats.
Moreover, the democratization of offensive cyber tools poses a significant challenge. These tools empower malicious actors to orchestrate low-sophistication attacks, putting immense pressure on security teams. Commercialization of cybercrime exacerbates this threat landscape, enabling attacks without substantial expertise.
AI emerges as a critical ally in the fight against cyber threats. Its continuous learning and adaptability allow it to analyze vast data volumes and identify anomalies in real-time, regardless of location within an organization’s infrastructure. Darktrace pioneers AI-driven threat detection, using Bayesian inference models to detect deviations from normal behavior.
In conclusion, cybersecurity is an ongoing battle against evolving threats. AI-driven solutions offer promise in bolstering defenses in today’s digital era. By embracing innovation and adopting a proactive stance, organizations can fortify resilience against cyber adversaries and safeguard digital assets effectively.
KnowBe4’s Cybersecurity Trends 2023

KnowBe4’s Team of Cybersecurity Experts Release Top Five Predictions for 2023
Anticipated Rise in Devastating Infrastructure Attacks
Experts predict an increase in devastating strikes on important infrastructure. Additionally, they anticipate significant outages as hackers target essential infrastructure, particularly amidst the ongoing conflict between Russia and Ukraine. This could have societal and economic repercussions for a sizable population or even an entire country. People might engage in digital civil disobedience by attacking their own national infrastructure or government websites as a means of protest in response to the global recession and rising cost of living.
Surge in Social Media Frauds
A surge in social media fraud represents a new field of social engineering combat. Scammers will proliferate on social media, endangering friends, family, organizations, and coworkers. As the social media commerce and marketplace industries continue to expand, people will increasingly rely on indicators of trust, such as the number of connections an account has and its activity duration, making them more vulnerable to scams that use stolen social media accounts to deceive. Scammers will undoubtedly exploit the fact that official verification is now available for a low cost on various platforms.
Emphasis on Establishing a Security Culture
There is a shift in emphasis toward establishing a security culture across enterprises worldwide. Most businesses now recognize the importance of security awareness training, and many are beginning to shift their focus from training alone to including behavior and culture. Building a robust security culture with the backing of leaders and the entire staff base has gained positive momentum globally.
Rise of Dangerous Deepfake Assaults
Dangerous deepfake assaults will become more convincing and harmful to reputations. Deepfakes are a risky method of gaining someone’s trust by getting them to take words and actions at face value in front of gullible individuals. Organizations do not yet adequately educate their personnel about the subject because they lack a thorough awareness of the risks this can pose to their reputation.
Expanding Attack Surface in the Metaverse
The increased attack surface of the Metaverse brings new dangers. It is becoming harder to fully secure enterprises worldwide due to more danger vectors, leading to a bigger attack surface. Cybercriminals now have additional options to launch assaults due to the growth of the Metaverse.
Stu Sjouwerman, CEO of KnowBe4, emphasized, “This list of predictions in cybersecurity trends has been gathered from our global group of experts who have decades of experience in the cybersecurity field. They are at the forefront of what is happening in the industry, constantly following trends and staying up to date on the latest threats, tools, and techniques. Many of them noted a fundamental shift in focus for organizations beyond security awareness training alone to striving for a strong security culture that is driven by measurable behavioral change. Also, social engineering will continue to dominate as an overwhelmingly successful method for cybercriminals to execute attacks.”
Lenovo Think Family
Smarter partners with business innovations
Over the years, the Think commercial products have become synonymous with innovation—not just for engineered devices, but more importantly, for what you create with them. Lenovo technology thinks big. From destroying cancer cells with precise real-time feedback in the operating room to feeding future generations through AI, we’re building smarter solutions for things that matter. Whether you’re looking to grow your company or you simply want reliability and design quality our Think products deliver, to help you succeed.
ThinkPad
Relentless innovation. Trusted quality. Purposeful design.
Featuring first-to-market technology that works smarter for you, our ThinkPad portfolio delivers reliability you can count on. All of our devices are MIL-SPEC tested against extreme conditions. We offer remote manageability options, as well as advanced security solutions with ThinkShield, an integrated suite of hardware and software. Enterprise-level support available to keep you up and running.
ThinkBook
Built for business, designed for you
Lightweight and stylish, Lenovo ThinkBooks offer seamless security and efficiencies. Features like Modern Standby and Smart Power On help to boost performance and improve productivity. Plus voice control, dual-screen designs, and enhanced audio put technology to work for your business. Includes SMB-grade support offerings.
ThinkStation
Superior reliability & performance
ThinkStation P Series workstations deliver powerful performance with the latest generation of Intel® Xeon® processors and NVIDIA® Quadro® professional graphics in dual- and single-processor systems. Independent software vendor (ISV) certified, energy-efficient, and highly versatile, our ThinkStations exemplify the superior reliability you expect from Think.
ThinkBook
Built for business, designed for you
Lightweight and stylish, Lenovo ThinkBooks offer seamless security and efficiencies. Features like Modern Standby and Smart Power On help to boost performance and improve productivity. Plus voice control, dual-screen designs, and enhanced audio put technology to work for your business. Includes SMB-grade support offerings.
ThinkVision
Superbly designed monitors
Equipped with features that enhance productivity for the modern workforce, ThinkVision monitors also boast sleek, ergonomic designs. Whether it’s factory calibration and sRGB color gamut, USB-C one-cable solutions, energy-efficiency, built-in audio, or the ease of configuring multi-display setups, these monitors are engineered with your comfort, convenience, and security in mind.
ThinkSmart
Smart office devices
Combining innovative technology with personalized services, our ThinkSmart solutions will redefine your meeting space. Make collaboration more productive and efficient with devices that offer flexible platforms and room sizes. Plus, built-in security keeps your data safe and your privacy intact. Take your business to the next level.
ThinkCentre
Industry-leading desktop innovation
We’ve engineered ThinkCentre desktops to accommodate the reality of shrinking office space. Our innovative designs include the phone-sized Nano, the industry-first 1L Tiny and Tiny-in-one, traditional tower PCs, and our all-in-ones. These PCs deliver superior performance, lifecycle stability, robust security, and premium support offerings.
ThinkShield
Security is in our DNA
At Lenovo, we take security seriously. ThinkShield is our comprehensive portfolio of security offerings based on the latest technology innovations. It’s your foundation of defense to help you prevent, detect, and recover from security attacks.
https://www.lenovo.com/us/en/?orgRef=https%253A%252F%252Fwww.google.com%252F
Knowbe4 Cybersecurity

Knowbe4 Cybersecurity
In the ever-evolving landscape of cybersecurity threats, staying ahead of cybercriminals requires a multifaceted approach. While endpoint protection and robust security software are crucial components of a defense strategy, they are not infallible. Cybercriminals continuously devise new tactics to breach defenses, often exploiting the weakest link in the security chain: human behavior.
Social engineering techniques, such as phishing emails and pretexting phone calls, prey on human vulnerabilities, manipulating individuals into divulging sensitive information or unwittingly facilitating access to secure systems. These tactics are increasingly sophisticated, leveraging psychological manipulation and exploiting trust to deceive even the most vigilant employees.
Organizations must recognize the critical importance of addressing the human element of cybersecurity through comprehensive security awareness training programs. Such programs educate employees about common cyber threats, teach best practices for identifying and responding to suspicious activity, and reinforce the importance of adhering to security protocols.
Furthermore, effective security awareness training goes beyond mere awareness to foster a culture of security within an organization. By empowering employees to become proactive participants in cybersecurity defense, organizations can significantly reduce the risk of successful cyberattacks.
In addition to training, regular assessments and simulations can help evaluate the effectiveness of security awareness efforts and identify areas for improvement. By continually refining and adapting security awareness initiatives in response to emerging threats and evolving employee needs, organizations can better mitigate the risk of cyber incidents and safeguard sensitive data and assets.
Ultimately, cybersecurity is a shared responsibility that extends beyond the IT department to encompass every individual within an organization. By prioritizing security awareness and investing in ongoing education and training, organizations can strengthen their defenses and better protect against the ever-present threat of cybercrime.
https://newtech.mt/cybersecurity/

Celebrates 30th Anniversary of ThinkSystem - Lenovo Infrastructure Solutions V3
New Comprehensive Infrastructure Portfolio Delivers Scalable Solutions to Accelerate the New Era of IT
Lenovo Infrastructure Solutions V3 delivers advanced ThinkSystem, ThinkAgile, and ThinkEdge servers and storage with next-generation AMD, Intel and Arm-based processors, NVIDIA AI Enterprise software and enhanced Lenovo ThinkShield security, equipping businesses with greater agility, resiliency and performance
New Lenovo XClarity One, a cloud-based, unified software management platform, provides an industry-first integration of TruScale Infrastructure-as-a-Service, Management-as-a-Service and Smarter Support analytics to simplify orchestration, automation and metering from edge to cloud
Next-generation Lenovo Neptune™ warm water cooling and CO2 Offset Services help customers achieve their sustainability goals
Lenovo today unveiled new end-to-end infrastructure solutions and services aimed at accelerating global IT modernization with cutting-edge performance, security, and sustainable computing capabilities. This marks the most comprehensive portfolio upgrade in Lenovo’s history.
For businesses of all sizes looking to deploy and manage hybrid multi-cloud and edge environments more easily, as well as traditional and artificial intelligence (AI) workloads across industries such as retail, manufacturing, financial services, healthcare, and telecom, the new Lenovo Infrastructure Solutions V3 portfolio offers market-leading innovations.
The launch coincides with the celebration of the ThinkSystem x86 server’s 30th anniversary. This significant milestone in enterprise computing technology facilitated an open innovation environment and heralded the current information era for enterprises. To help businesses capitalize on the new era of IT, Lenovo’s new Infrastructure Solutions V3 portfolio features a distinctive open architecture with enhanced administration, greater reliability, and expanded security.
In addition, Lenovo introduces new transition words throughout the passage to improve flow and coherence.
Empower Your Productivity with Aspire 5

Make. It. Happen.
Elevate your computing experience with the latest 12th Gen Intel® Core™ i7 processors powering the Aspire 5, engineered for multitasking prowess and unparalleled productivity. With the added punch of the NVIDIA® GeForce® RTX2050, dive into accelerated photo and video editing like never before.
Keep Your Cool
Efficiency meets innovation with engineered cooling solutions that push the boundaries of performance. Dual fans, coupled with multiple cooling modes and dual copper thermal pipes, ensure optimal temperature management, even during intense sessions. Plus, with the air inlet keyboard expelling up to 10% more heat, your system stays cool under pressure.
Display Your Best
Unleash your creativity on a canvas of brilliance with the optional touch screen and your choice of FHD or QHD display. Revel in the immersive visual experience, boasting a screen-to-body ratio of 81.18%, complemented by Acer’s visual innovations for dynamic color adjustment and comfortable viewing.
The Smarts
Unlock a world of possibilities with cutting-edge features like Acer TNR Solution, providing low-light image noise reduction for crystal-clear visuals. Elevate your communication with Acer PurifiedVoiceTM, actively reducing background noise for pristine audio, whether you’re using external headphones or microphones.
The Connectivity
Stay ahead of the curve with Wi-Fi 6E and Bluetooth® 5.2, delivering lightning-fast file sharing and seamless 4K streaming. Need more screen real estate? Harness the power of Thunderbolt 4 to connect two 4K monitors for next-level multitasking.
The Design
Crafted with precision, the Aspire 5 boasts a sleek metal cover and an ergonomically designed elevating hinge for enhanced comfort and style. Available in a spectrum of colors to suit your individual taste, and featuring an optional illuminated keyboard, empower yourself to accomplish more from anywhere, anytime.

Razer Iskur Gaming Chair
The Perfect Gaming Form !
ERGONOMIC GAMING CHAIR WITH INTEGRATED LUMBAR SUPPORT
The Razer Iskur provides total lower back support. It features an integrated, fully adjustable lumbar curve that closely aligns with your spine. Unlike most gaming chairs, which have lumbar pillows that shift over time or fixed supports that can’t be adjusted, this ensures ideal gaming posture for maximum comfort during gaming marathons.
MULTI-LAYERED SYNTHETIC LEATHER FOR AN ERGONOMIC EXPERIENCE
Additionally, this ergonomic gaming chair features material that is soft and comfortable to the touch. It is also more resilient and long-lasting than regular PU leather, better suited to handle the peeling that results from prolonged daily usage.
HIGH DENSITY FOAM CUSHIONS FOR COMFORT AND SUPPORT
Moreover, the soft, deep cushions on the Razer Iskur enable greater contouring. They allow your weight to apply exactly the right amount of pressure as they conform to accommodate your particular body shape, providing the ideal combination of support and comfort.
4D ARMRESTS FOR CUSTOMIZABLE COMFORT
Enjoy fully customizable positioning with armrests that you can adjust up and down, forwards and backwards, left and right, and rotate inwards or outwards.
ENGINEERED TO CARRY: ROBUST DESIGN FOR GAMING ENTHUSIASTS
This ergonomic gaming chair has a steel-reinforced body, armrests, and wheelbase to hold up to 299lbs/136kg of weight. It’s best for players who are between the heights of 5’6″ and 6’2″/170 and 190cm. Additionally, to increase the amount of surface area for reclining, it also has inclined seat edges.
MEMORY FOAM HEAD CUSHION FOR ADDED SUPPORT
Furthermore, the Razer Iskur comes with a head cushion made of highly dense yet malleable memory foam. It molds to the shape of your head for the right amount of support and comfort.