Email Vigilance Checklist: Safeguarding Your Inbox
Email Vigilance Checklist: Safeguarding Your Inbox
In today’s digital age, email has become an indispensable tool for communication in both personal and professional spheres. However, with the convenience of email also comes the risk of cyber threats such as phishing, malware, and spoofing. To protect yourself and your organization from these dangers, it’s crucial to adopt robust email security practices. Here are some essential tips to help you safeguard your inbox:
Validate Sender Information:
Always scrutinize the ‘from’ field of an email to verify the sender’s identity. Keep in mind that malicious actors can easily spoof email addresses to deceive recipients. If an email seems suspicious or unexpected, double-check the sender’s details before taking any further action.
Exercise Caution with Attachments:
Be cautious when opening email attachments, particularly those with executable file extensions such as ‘.exe’. A general rule of thumb is to avoid opening attachments from unknown or untrusted sources. Additionally, be wary of files with double extensions (e.g., ‘safe.txt.exe’), as they could contain harmful malware.
Report Suspicious Activity:
If you receive an email that raises suspicions or appears to be a phishing attempt, report it immediately to your organization’s IT help desk or security team. Prompt reporting can help prevent potential security breaches and protect other users within your organization.
Verify Hyperlinks:
Before clicking on any hyperlinks embedded in an email, hover your mouse cursor over the link to preview the URL. Watch out for discrepancies between the displayed URL and the actual destination. Be especially cautious of hyperlinks that lead to unfamiliar or suspicious websites, as they could be phishing sites designed to steal your personal information.
Stay Vigilant Against Domain Spoofing:
Cybercriminals often use domain spoofing techniques to create fraudulent websites that mimic legitimate ones. Pay close attention to the domain name in email links and be wary of subtle variations or misspellings. For example, ‘www.bankofarnerica.com‘ may appear similar to the legitimate ‘www.bankofamerica.com‘, but it could lead to a malicious site.
By adhering to these email security best practices, you can significantly reduce the risk of falling victim to cyber threats and protect your sensitive information. Remember, maintaining a vigilant and cautious approach to email communication is key to safeguarding both your personal and professional digital assets.
If you have any further questions or concerns about email security, don’t hesitate to reach out to your organization’s IT support team for assistance. Stay safe, stay secure!

Red Flags - Stay Alert and Stay Safe
Red Flags – Social Engineering
Identify Red Flags in an Email
Identifying red flags in an email is crucial to stay alert and stay safe from social engineering attacks. Here’s a breakdown of what to look out for:
Stay Alert: Red Flags From the Sender:
- First and foremost, check if the sender’s email address is unfamiliar or unrelated to your usual contacts.
- Additionally, scrutinize whether the email is from someone outside your organization, not related to your job responsibilities.
- Equally important is to assess if the email is from someone inside your organization, but the content is unusual or out of character.
- Furthermore, watch out for suspicious sender email domains, like “micorsoft support.com.”
- Moreover, consider if there’s a lack of personal acquaintance or endorsement from someone you trust.
- Take note if there’s no prior business relationship or communication history with the sender.
- Lastly, be wary of unexpected or unusual content, especially with embedded hyperlinks or attachments.
Stay Safe: Spotting Suspicious Hyperlinks:
- It’s important to mention that hovering over a hyperlink reveals a different destination URL, a significant red flag.
- Another key point is that emails with only long hyperlinks and no further context or content are suspicious.
- Additionally, be cautious of misspelled hyperlinks mimicking known websites, such as “www.bankofarnerica.com.”
Stay Vigilant: Identifying Unusual Recipients and Attachments:
- Consider whether you’ve been cc’d on an email to unfamiliar recipients.
- Additionally, be cautious of emails sent to an unusual mix of people, such as random groups or unrelated addresses.
- Look out for unexpected or nonsensical attachments, especially from senders who don’t typically send such files.
- Also, be cautious of attachments with potentially dangerous file types, with .txt files being the only inherently safe type.
Stay Aware: Timing, Subject Lines, and Content:
- It’s worth noting if emails are received at unusual times, especially outside regular business hours.
- Take note of irrelevant subject lines or subject lines that don’t match the email content.
- Similarly, be cautious of emails that appear as replies to unrequested or unsent messages.
- Pay attention to requests to click on links or open attachments under the threat of negative consequences or with promises of gain.
- Also, watch out for unusual or poor grammar and spelling errors in the email.
- Additionally, consider whether there are illogical or suspicious requests to click on links or open attachments.
- Trust your instincts if you sense discomfort or suspicion regarding the email’s content.
- Lastly, be cautious of emails requesting viewing of compromising or embarrassing images.
By being vigilant and attentive to these red flags, you can protect yourself and your organization from falling victim to social engineering attacks.
Enhancing Cybersecurity - Continuous Cyber AI Loop
Darktrace’s technology vision is a continuous, Cyber AI Loop™, where each capability autonomously feeds back into the system as a whole, continuously improving the state of cyber security.
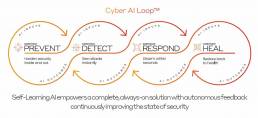
Improving Awareness and Decision-Making
From the attacker's perspective, Darktrace PREVENT provides vital insights to defenders. Consequently, it enables them to identify existing devices that are externally facing or part of a critical attack path, enhancing their overall awareness of the environment.
Moreover, users benefit from contextual information about external facing assets and critical attack paths via tags in the DETECT and RESPOND user interface. This enables better decisions, quicker triage, and facilitates further modeling using this new information. For example, if PREVENT identifies a web server on a critical attack path, relevant entities receive tags in DETECT, providing crucial knowledge for detection modeling and AI Analyst investigations.
Incorporating Industry Standards for Faster Understanding
Darktrace incorporates the MITRE ATTACK Framework across the loop. Additionally, it tags devices identified by Darktrace PREVENT as sitting on a critical attack path with MITRE techniques corresponding to the inbound and outbound parts of the attack path. This provides automatic mapping to an industry-standard attack framework for auditing, compliance, and faster understanding of all components of the attack.
Richer AI Analyst Investigations
AI Analyst investigations become richer as they enrich existing investigations with malicious hostnames retrieved from PREVENT/ASM. Consequently, this indicates they are more likely to be suspicious and potentially part of an incident.
Heightening Email Security
Darktrace PREVENT/Attack Surface Management informs Darktrace/Email of potential threats, such as domain spoofing. This action heightens sensitivity around these assets and takes action when these spoof domains are used for malicious purposes. Hence, this leads to more accurate decision-making in the email realm, reducing analysis time for individual emails.
Consolidating Insights for Better Response
Assets confirmed as malicious by Darktrace PREVENT/Attack Surface Management automatically become ‘Watched Domains’ in Darktrace/Network. This enhancement enables security teams to consolidate insights from inside the business and externally on the attack surface in a single pane of glass, improving their ability to respond effectively.
KnowBe4 Security Awerness Training
KnowBe4 Security Awerness Training
KnowBe4 Security Awareness Training, the largest complete Security Awareness Training and Simulated Phishing platform in the world, has more than 50,000 users. With this platform, you now have a comprehensive solution to better manage IT security issues, including social engineering, spear phishing, and ransomware assaults.
Training and Testing Features:
KnowBe4 offers self-service enrollment. Additionally, it provides world-class, user-friendly new-school security awareness training. Furthermore, it offers pre-and post-training phishing security tests to reveal the proportion of end users that are Phish-prone. Moreover, KnowBe4’s very efficient, regular, random Phishing Security Tests offer several corrective measures.
Assessment and Evaluation:
Utilize KnowBe4 Assessments to evaluate your users’ security awareness skills and the broader security culture of your company. These evaluations assist you in modifying training to meet knowledge gaps and weaknesses. Additionally, they help in tracking the effects of your security awareness training program on enhancing users’ security awareness knowledge and attitudes over time.
Benchmarking and Comparison:
You can contrast your organization’s security awareness proficiency results with those of other businesses in your sector using the tools of the Security Awareness Proficiency Assessment and Security Culture Survey. Examine your organization’s performance in relation to the seven security knowledge areas and the seven dimensions of security culture using the results of your baseline assessment and survey. Also, keep track of how well your organization is doing over time.
User Experience Enhancements:
With the updated end-user security awareness training interface, your users will enjoy a brand-new learning environment that makes learning enjoyable and engaging. Additionally, you can provide your users with 24/7 access to assigned training via the KnowBe4 Learner App. This makes it simple for them to learn whenever and wherever they want. Moreover, the localized training interface for KnowBe4 is offered in a variety of languages, allowing your users to select the one they feel most at ease using for an immersive training experience.
Customization Options:
If you want to add custom training or other corporate training materials to the KnowBe4 security awareness training materials, you can now do so. You can manage both your own SCORM-compliant training and video materials in one location, together with the KnowBe4 ModStore training material.
Risk Detection and Reporting:
You may begin to detect risk at the user, group, and organizational levels with the new Virtual Risk Officer and Advanced Reporting tools. These tools will assist you in making data-driven decisions regarding your security awareness plan. Additionally, you may assess the success of your security awareness training program by looking at next-level reporting for simulated phishing and security awareness training campaigns.
Automated Program Implementation:
When it comes to developing a security awareness program that will work for their firm, many IT professionals are unsure about where to begin. With the help of our Automated Security Awareness Program, we have eliminated all the uncertainty. If you want to implement all the procedures to establish a comprehensive security awareness training program for your firm quickly, ASAP enables you to create a bespoke curriculum for it.
Develop Your Users
The greatest collection of security awareness training materials available anywhere in the globe, including newsletters, interactive modules, movies, games, and posters. automated reminder emails for training campaigns.
Phish Your Users
Thousands of templates with limitless use and best-in-class, fully automated simulations of phishing assaults.
See The Results
Management-ready, enterprise-strength reporting with statistics and graphs for security awareness training and phishing. Show the fantastic ROI!
AI threat detection that ‘understands you’ critical to thwarting attacks
Detection is crucial in cybersecurity, but it’s just one aspect of today’s complex landscape. Threat actors leverage open-source code, AI, and MFA as potent weapons, necessitating continuous and adaptive security measures across an organization’s digital ecosystem.
Toby Lewis, from Darktrace, emphasizes AI’s role in threat detection. This technology comprehends organizational behavior and establishes a baseline of normalcy. It discerns known and unknown threats, making real-time decisions to mitigate risks effectively.
Lewis highlights the relentless pace and complexity of cyberattacks, necessitating a proactive defense strategy. Despite efforts, it’s challenging to monitor every digital aspect simultaneously. With cloud computing, SaaS, and IoT, the attack surface expands, leaving enterprises vulnerable to diverse threats.
Moreover, the democratization of offensive cyber tools poses a significant challenge. These tools empower malicious actors to orchestrate low-sophistication attacks, putting immense pressure on security teams. Commercialization of cybercrime exacerbates this threat landscape, enabling attacks without substantial expertise.
AI emerges as a critical ally in the fight against cyber threats. Its continuous learning and adaptability allow it to analyze vast data volumes and identify anomalies in real-time, regardless of location within an organization’s infrastructure. Darktrace pioneers AI-driven threat detection, using Bayesian inference models to detect deviations from normal behavior.
In conclusion, cybersecurity is an ongoing battle against evolving threats. AI-driven solutions offer promise in bolstering defenses in today’s digital era. By embracing innovation and adopting a proactive stance, organizations can fortify resilience against cyber adversaries and safeguard digital assets effectively.