Empowering Cybersecurity Simplification-Underdefense

In an era where digital threats loom large and security breaches are a constant concern for businesses of all sizes, UnderDefense introduces a game-changing solution: the MAXI Platform. Offering a holistic Security-as-a-Service (SECaaS) approach, this platform stands as the ultimate one-stop-shop for security and compliance needs.
Unlocking Cybersecurity Simplification for Enhanced Business Growth
The UnderDefense MAXI Platform is a product of extensive industry expertise. Consequently, it’s designed to empower organizations regardless of their size. Furthermore, it offers 24/7/365 end-to-end protection, detection, and response capabilities, making cybersecurity an effortless endeavor.
Ensuring Complete Security Measures: A Step-by-Step Guide
- Monitoring Excellence: Gain unparalleled visibility into your digital ecosystem. This ensures swift identification and response to any suspicious activity round the clock.
- Compliance Made Easy: Seamlessly integrate SIEM, Cloud, and EDR platforms. Additionally, utilize pre-built templates to adhere to the most stringent regulatory requirements without straining your resources.
- Automated Security: Enhance efficiency by automating routine security processes. This allows your team to focus on strategic initiatives while fortifying your defenses.
- Integration Flexibility: Irrespective of your existing digital infrastructure, the MAXI Platform smoothly integrates with over 45 legacy systems. Consequently, it eliminates the need for coding or redevelopment.
- Alert Optimization: Combat alert fatigue by filtering out false positives. Thus, ensuring that critical alerts are promptly addressed for a secure environment without overwhelming your team.
- Cost Optimization: Consolidate enterprise-wide protection under a single SECaaS solution. This enables a seamless setup without additional hires or hidden expenses. Transparent pricing ensures scalability without unexpected costs.
Leveraging the MAXI Platform: Your Competitive Security Edge
The brilliance of the UnderDefense MAXI Platform lies in its simplicity. By providing an all-encompassing solution, it eliminates the complexity of cybersecurity operations. Consequently, allowing organizations to focus on growth and innovation without compromising on security.
Tailored for All
Whether you’re a startup or an established enterprise, the MAXI Platform is tailored to meet your security needs. Offering a proactive, scalable, and affordable solution, it ensures that every business can fortify its defenses against modern cyber threats.
Future-Proof Security
Cyber threats evolve constantly. However, with the MAXI Platform, businesses gain a future-proof security strategy. The platform adapts and evolves alongside emerging threats. Hence, providing peace of mind and confidence in an ever-changing digital landscape.
Partnering for Success
UnderDefense doesn’t just offer a product; it’s a partner in your journey towards a secure future. With constant support, regular updates, and a commitment to staying ahead of the curve, it stands as a reliable ally in the fight against cyber threats.
The UnderDefense MAXI Platform represents a paradigm shift in the world of cybersecurity. By simplifying, unifying, and enhancing security operations, it enables organizations to navigate the digital realm with confidence and focus on what truly matters: growth, innovation, and success.
In a world where cyber threats are a constant battle, the MAXI Platform emerges as a beacon of comprehensive protection, ensuring that businesses thrive securely in the digital age.
Underdefence: Your Ultimate Cybersecurity Defender
In the current digital age, where businesses thrive on interconnected systems and data, the need for robust cybersecurity measures has never been more critical. Cyber threats loom large, posing significant risks to sensitive information and organizational integrity. Recognizing these challenges, UnderDefence emerges as a reliable partner, offering a comprehensive suite of cybersecurity services aimed at fortifying your defenses against evolving threats.
Unveiling UnderDefence's Holistic Cybersecurity Arsenal

Empower Your Team’s Cybersecurity with SecurityCoach from KnowBe4
Eliminating Mediators, Amplifying Expertise
By bypassing middlemen or outsourcers, UnderDefence positions itself as a cybersecurity heavyweight with a plethora of knowledge and expertise. Consequently, with this strategy, you can be sure that services will be provided directly and with excellent quality, maximizing efficiency and dependability in protecting your digital assets.
Managed Detection and Response: Uninterrupted Vigilance
Cyber threats are always changing and require constant observation. Therefore, UnderDefence continuously monitors your endpoints, providing you with a thorough picture of any potential security holes. Prompt action against potential backdoors stops hackers from gaining access to your system, thereby preventing them from attempting to undermine the integrity of your business.
Penetration Testing: Thwarting Vulnerabilities
Preventive actions are the cornerstone of a strong cybersecurity posture. Accordingly, UnderDefence uses manual penetration testing to examine your product source code and infrastructure in great detail. Consequently, the ensuing comprehensive analysis pinpoints weaknesses and provides tactical suggestions to strengthen security gaps efficiently.
Incident Response: Rapid Resolution, Swift Recovery
In cases of emergency, UnderDefence’s security squad is ready to go in the terrible case of a security breach. In cases involving encryption or data theft, prompt and accurate incident reaction is essential. Their knowledge not only fixes current problems but also strengthens your cybersecurity system to fend off intrusions in the future, guaranteeing a quick recovery and little interruption to business operations.
The UnderDefence Advantage: Unmatched Expertise, Proactive Solutions
In addition to offering services, UnderDefence provides peace of mind. They take a proactive approach to cybersecurity that goes beyond countering existing dangers. This proactive approach gives companies the ability to remain ahead of the curve in the cybersecurity space by strengthening defenses against new threats and constantly adapting.
Safeguarding Tomorrow’s Success Today
UnderDefence offers peace of mind in addition to services. They take a proactive approach to cybersecurity that goes beyond countering existing
Lenovo - Sustainability and Leadership

In a remarkable acknowledgment of its commitment to sustainability, Lenovo has been crowned a “Champion” vendor in the prestigious 2023 Canalys Global Sustainable Ecosystems Leadership Matrix. This recognition underscores Lenovo’s outstanding achievements in sustainability-focused partner programs and its robust organizational strategies.
A Pinnacle of Excellence
Lenovo stands among the top three industry vendors to attain the highest Champion status, a testament to its strong portfolio of sustainability solutions and unwavering dedication to decarbonization commitments. Moreover, this award reflects positive sentiments from the IT channel, highlighting Lenovo’s impactful sustainability initiatives.
A Legacy of Sustainability
Lenovo’s journey in sustainability dates back to 2008 when it published its first sustainability report. Since then, the company has consistently demonstrated leadership by being among the first to receive validation for its net-zero targets from the Science Based Targets initiative. This legacy of action underscores Lenovo’s ongoing dedication to environmental responsibility.
The Lenovo 360 Circle: Fostering Collaboration for a Sustainable Future
At the heart of Lenovo’s sustainability endeavors is the Lenovo 360 Circle. This global channel framework brings together partners to align on Environmental, Social, and Governance (ESG) objectives. Furthermore, the Lenovo 360 Circle serves as a platform for collaboration, encouraging partners to share best practices and collectively address sustainability challenges. Virginie Le Barbu, Lenovo’s Global Sustainability Director, expressed pride in leading the way with the Lenovo 360 Circle, emphasizing the importance of collaboration in driving sustainable impacts efficiently.
Sustainability as an Expectation
Pascal Bourguet, Lenovo’s Global Channel Chief, highlighted that sustainability is no longer an exception but an expectation. The Lenovo 360 global partner framework places sustainability solutions at the forefront of key business outcomes that partners can provide for their customers. Consequently, this approach reflects Lenovo’s commitment to integrating sustainability into the core of its business operations.
Beyond Recognition: Delivering Sustainable Services
In addition to its recognition in the Canalys Global Sustainable Ecosystems Leadership Matrix, Lenovo continues to innovate in sustainability services. For instance, the recently announced Reduced Carbon Transport service exemplifies Lenovo’s dedication to offering practical and impactful solutions for its customers.
Canalys Global Sustainable Ecosystems Leadership Matrix
The Canalys Global Sustainable Ecosystems Leadership Matrix is a comprehensive evaluation that considers 14 vendors based on their commitment and progress in driving sustainability in the partner ecosystem over the past 12 months. Lenovo’s recognition as a Champion reflects the company’s holistic approach. This approach combines ecosystem feedback, survey data, and independent assessments by Canalys analysts.
A Smarter, Inclusive, and Trustworthy Future
Lenovo, a US$62 billion revenue global technology powerhouse, is not just a leader in sustainability but also a force driving the advancement of ‘New IT’ technologies. With a bold vision to deliver smarter technology for all, Lenovo is building a more inclusive, trustworthy, and smarter future for everyone, everywhere.
For more details on Lenovo’s sustainability initiatives, including the Canalys Global Sustainable Ecosystems Leadership Matrix, and to explore the latest in Lenovo’s innovation, visit Lenovo’s official website.
Cybersecurity Awareness Month - October

October is Cybersecurity Awareness Month
As we reach the middle of October, we find ourselves firmly in the heart of Cybersecurity Awareness Month. This is the perfect time to reflect on what we’ve learned and reiterate the importance of staying cyber-savvy. In a world where digital threats constantly evolve, staying informed and vigilant is paramount.
Mid-October Cybersecurity Checklist:
To ensure you’re on the right track in protecting your digital life, here’s a mid-October cybersecurity checklist:
- Review Your Passwords: Take some time to revisit your passwords. Are they strong and unique? Have you enabled 2FA wherever possible? If not, make the necessary changes.
- Check for Software Updates: Go through your devices and software applications. Make sure they’re all up to date. Cybercriminals often target vulnerabilities in outdated software.
- Phishing Awareness: Reiterate the importance of being cautious with emails, especially those from unknown senders. Double-check any suspicious links or attachments. Don’t let your guard down.
- Back Up Your Data: If you haven’t done so yet, set up a regular backup routine for your important data. This can be a lifesaver in the event of data loss due to cyberattacks.
- Stay Informed: Continue to educate yourself about emerging cybersecurity threats. Follow cybersecurity news, blogs, and resources to stay up-to-date.
- Family and Friends: Share your cybersecurity knowledge with friends and family. Many cybercrimes target less tech-savvy individuals, so help protect your loved ones too.
As we mark the midpoint of Cybersecurity Awareness Month, it’s a great time to take stock of your online security practices. By staying vigilant and following the best practices mentioned earlier in the month, you’re already on your way to a safer online experience.
Remember that cybersecurity is an ongoing effort. The threats keep evolving, and so should your defenses. Make it a habit to regularly update your knowledge and security measures. Your digital well-being is worth the effort, and you play a crucial role in creating a safer online environment.
Get Your Free Cybersecurity Awareness Month Resource Kit Now!
Cybersecurity Awareness Month

Cybersecurity Awareness Month!
Cybersecurity Awareness Month

Cybersecurity Awareness Month!
raising awareness about cybersecurity is crucial, especially during Cybersecurity Awareness Month. It’s a time when the spotlight shines on the importance of staying vigilant against cyber threats. Imagine malware lurking in an innocent-looking email, just waiting for someone to click. It’s like inviting the monsters under your bed into your network; spear phishing witches, ransomwolves, you name it!
But don’t panic just yet! While torches and pitchforks won’t solve this modern-day dilemma, fostering a resilient security culture within your organization can work wonders. That’s why we’re excited to share these invaluable resources from our partner KnowBe4, designed to fortify your cybersecurity defenses throughout October.
Here’s what’s in store for you:
- Access to a treasure trove of free resources, including KnowBe4’s most sought-after on-demand webinar and whitepaper.
- Handy planning tools, such as your Cybersecurity Awareness Month User Guide and Cybersecurity Awareness Weekly Planner.
- Brand new video content like “Security Culture and You,” along with eight more engaging modules available in multiple languages.
- Four informative security hints and tips newsletters, supplemented by additional security documents and awareness tips, all in multiple languages.
- Plus, dive into the realm of cyber-monsters with five character cards and posters, alongside other eye-catching assets in multiple languages.
In addition to these resources, it’s essential to highlight the significance of continuous education and training in cybersecurity. Threats are constantly evolving, and so should our defenses. Encouraging employees to stay informed about the latest trends in cyber attacks and best practices for preventing them can significantly enhance your organization’s security posture.
Furthermore, consider organizing interactive workshops or simulations to simulate real-world cyber threats and test employees’ responses. These hands-on experiences can help reinforce cybersecurity concepts and empower individuals to recognize and respond effectively to potential threats.
Remember, cybersecurity is everyone’s responsibility. By fostering a culture of security awareness and providing the necessary resources and support, we can collectively strengthen our defenses against cyber threats and protect our valuable assets.
Get Your Free Cybersecurity Awareness Month Resource Kit Now!
Get Your Kit!

Authorized Service Centre for Lenovo, Acer, and MSI

Providing Reliable Service:
Authorized Service Center for Lenovo, Acer, and MSI
In today’s world, having access to reliable and efficient service centers is crucial for customers who encounter issues with their electronic devices. We are proud to announce that our service center has earned the prestigious status of being an authorized service center for three leading technology brands: Lenovo, Acer, and MSI. This achievement reflects our commitment to providing high-quality repair and maintenance services to our valued customers.
Expertise and Accreditation
Becoming an authorized service center involves strict requirements and demonstrating expertise in handling products from these renowned brands. Firstly, we have gone through a strict evaluation process, ensuring that we have the necessary technical knowledge, infrastructure, and genuine spare parts to offer quality service.
Moreover, our team of highly trained technicians possesses in-depth knowledge about Lenovo, Acer, and MSI devices. Whether it’s a malfunctioning laptop, a tablet with a cracked screen, or a gaming PC in need of an upgrade, we have the expertise to diagnose and resolve issues efficiently. Our technicians stay up to date with the latest product developments, furthermore, troubleshooting techniques, and repair methodologies through continuous training provided by the manufacturers.
Skilled Technicians and Continuous Training
Our team of highly trained technicians possesses in-depth knowledge about Lenovo, Acer, and MSI devices. Whether it’s a malfunctioning laptop, a tablet with a cracked screen, or a gaming PC in need of an upgrade, we have the expertise to diagnose and resolve issues efficiently. Our technicians stay up to date with the latest product developments, troubleshooting techniques, and repair methodologies through continuous training provided by the manufacturers.
Access to Official Tools and Genuine Parts
Additionally, as an authorized service center, we have access to official repair tools, diagnostic software, and genuine parts provided directly by Lenovo, Acer, and MSI. This ensures that we can perform repairs and replacements using original components, maintaining the integrity and performance of the devices.
Warranty Support and Customer Satisfaction
Customers who bring their Lenovo, Acer, and MSI products to our service center can enjoy the benefits of warranty support. We handle warranty claims efficiently, furthermore, we stick to the manufacturers’ guidelines and processes. Consequently, with our authorized status, customers can have peace of mind knowing that their devices are being serviced by professionals who understand the intricacies of the products.
Transparent Service and Trust
Our focus is customer satisfaction. Therefore, we strive to provide a smooth experience to our customers, ensuring prompt service, clear communication, and transparent pricing. By offering authorized service, we instill trust in our customers, thus assuring them that their devices are in capable hands and will be repaired to the highest standards.
Exceptional Service for Lenovo, Acer, and MSI Customers
As an authorized service center for Lenovo, Acer, and MSI, we are committed to delivering reliable, efficient, and professional repair services. Our expertise gives us access to official tools and genuine parts, and our loyalty to warranty support guidelines set us apart from unauthorized service providers.
We invite Lenovo, Acer, and MSI customers to experience our exceptional service and trust us with their valuable devices.
Explore the Unknown - Password Guide
Tips For Password Security
The guidelines and steps for creating strong and secure passwords.
- Keep your passwords private – never share a password with anyone else
- Do not write down your passwords, use a password manager instead
- Use passwords of at least eight (8) characters or more (longer is better)
- Use a combination of upper case letters, lower case letters, numbers, and special characters (for example: !, @, &, %, +) in all passwords
- Avoid using people’s or pet’s names, or words found in the dictionary; it’s also best to avoid using key dates (birthdays, anniversaries, etc.)
- Substituting look-alike characters for letters or numbers is no longer sufficient (for example, Password” and “P@ssw0rd”)
- A strong password should look like a series of random characters
How To Create A Strong, Complex Password
Here’s a way to make a strong password that’s very hard to crack:
FOLLOW THESE STEPS
- Think of a phrase or sentence with at least eight words. It should be something easy for you to remember but hard for someone who knows you to guess. It could be a line from a favorite poem, story, movie, song lyric, or quotation you like.
Example:
I Want To Put A Dent In The Universe
- Remove all but the first letter of each word in your phrase.
IWTPADITU
- Replace several of the upper-case letters with lower case ones, at random.
iWtpADitU
- Now substitute a number for at least one of the letters. (Here, we’ve changed the capital “I” to the numeral 1).
iWtpAD1tU
- Finally, use special characters ( $, &, +, !, @) to replace a letter or two — preferably a letter that is repeated in the phrase. You can also add an extra character to the mix. (Here, we’ve replaced the “t” with “+”, and added an exclamation point at the end.)
iW+pAD1tU!
Why This Is Important ?
Traditional passwords can be cracked by hackers in less than a minute! Follow this guide to create passwords that would take centuries to crack.

Email Vigilance Checklist: Safeguarding Your Inbox
Email Vigilance Checklist: Safeguarding Your Inbox
In today’s digital age, email has become an indispensable tool for communication in both personal and professional spheres. However, with the convenience of email also comes the risk of cyber threats such as phishing, malware, and spoofing. To protect yourself and your organization from these dangers, it’s crucial to adopt robust email security practices. Here are some essential tips to help you safeguard your inbox:
Validate Sender Information:
Always scrutinize the ‘from’ field of an email to verify the sender’s identity. Keep in mind that malicious actors can easily spoof email addresses to deceive recipients. If an email seems suspicious or unexpected, double-check the sender’s details before taking any further action.
Exercise Caution with Attachments:
Be cautious when opening email attachments, particularly those with executable file extensions such as ‘.exe’. A general rule of thumb is to avoid opening attachments from unknown or untrusted sources. Additionally, be wary of files with double extensions (e.g., ‘safe.txt.exe’), as they could contain harmful malware.
Report Suspicious Activity:
If you receive an email that raises suspicions or appears to be a phishing attempt, report it immediately to your organization’s IT help desk or security team. Prompt reporting can help prevent potential security breaches and protect other users within your organization.
Verify Hyperlinks:
Before clicking on any hyperlinks embedded in an email, hover your mouse cursor over the link to preview the URL. Watch out for discrepancies between the displayed URL and the actual destination. Be especially cautious of hyperlinks that lead to unfamiliar or suspicious websites, as they could be phishing sites designed to steal your personal information.
Stay Vigilant Against Domain Spoofing:
Cybercriminals often use domain spoofing techniques to create fraudulent websites that mimic legitimate ones. Pay close attention to the domain name in email links and be wary of subtle variations or misspellings. For example, ‘www.bankofarnerica.com‘ may appear similar to the legitimate ‘www.bankofamerica.com‘, but it could lead to a malicious site.
By adhering to these email security best practices, you can significantly reduce the risk of falling victim to cyber threats and protect your sensitive information. Remember, maintaining a vigilant and cautious approach to email communication is key to safeguarding both your personal and professional digital assets.
If you have any further questions or concerns about email security, don’t hesitate to reach out to your organization’s IT support team for assistance. Stay safe, stay secure!

Red Flags - Stay Alert and Stay Safe
Red Flags – Social Engineering
Identify Red Flags in an Email
Identifying red flags in an email is crucial to stay alert and stay safe from social engineering attacks. Here’s a breakdown of what to look out for:
Stay Alert: Red Flags From the Sender:
- First and foremost, check if the sender’s email address is unfamiliar or unrelated to your usual contacts.
- Additionally, scrutinize whether the email is from someone outside your organization, not related to your job responsibilities.
- Equally important is to assess if the email is from someone inside your organization, but the content is unusual or out of character.
- Furthermore, watch out for suspicious sender email domains, like “micorsoft support.com.”
- Moreover, consider if there’s a lack of personal acquaintance or endorsement from someone you trust.
- Take note if there’s no prior business relationship or communication history with the sender.
- Lastly, be wary of unexpected or unusual content, especially with embedded hyperlinks or attachments.
Stay Safe: Spotting Suspicious Hyperlinks:
- It’s important to mention that hovering over a hyperlink reveals a different destination URL, a significant red flag.
- Another key point is that emails with only long hyperlinks and no further context or content are suspicious.
- Additionally, be cautious of misspelled hyperlinks mimicking known websites, such as “www.bankofarnerica.com.”
Stay Vigilant: Identifying Unusual Recipients and Attachments:
- Consider whether you’ve been cc’d on an email to unfamiliar recipients.
- Additionally, be cautious of emails sent to an unusual mix of people, such as random groups or unrelated addresses.
- Look out for unexpected or nonsensical attachments, especially from senders who don’t typically send such files.
- Also, be cautious of attachments with potentially dangerous file types, with .txt files being the only inherently safe type.
Stay Aware: Timing, Subject Lines, and Content:
- It’s worth noting if emails are received at unusual times, especially outside regular business hours.
- Take note of irrelevant subject lines or subject lines that don’t match the email content.
- Similarly, be cautious of emails that appear as replies to unrequested or unsent messages.
- Pay attention to requests to click on links or open attachments under the threat of negative consequences or with promises of gain.
- Also, watch out for unusual or poor grammar and spelling errors in the email.
- Additionally, consider whether there are illogical or suspicious requests to click on links or open attachments.
- Trust your instincts if you sense discomfort or suspicion regarding the email’s content.
- Lastly, be cautious of emails requesting viewing of compromising or embarrassing images.
By being vigilant and attentive to these red flags, you can protect yourself and your organization from falling victim to social engineering attacks.
Enhancing Cybersecurity - Continuous Cyber AI Loop
Darktrace’s technology vision is a continuous, Cyber AI Loop™, where each capability autonomously feeds back into the system as a whole, continuously improving the state of cyber security.
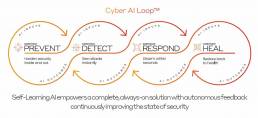
Improving Awareness and Decision-Making
From the attacker's perspective, Darktrace PREVENT provides vital insights to defenders. Consequently, it enables them to identify existing devices that are externally facing or part of a critical attack path, enhancing their overall awareness of the environment.
Moreover, users benefit from contextual information about external facing assets and critical attack paths via tags in the DETECT and RESPOND user interface. This enables better decisions, quicker triage, and facilitates further modeling using this new information. For example, if PREVENT identifies a web server on a critical attack path, relevant entities receive tags in DETECT, providing crucial knowledge for detection modeling and AI Analyst investigations.
Incorporating Industry Standards for Faster Understanding
Darktrace incorporates the MITRE ATTACK Framework across the loop. Additionally, it tags devices identified by Darktrace PREVENT as sitting on a critical attack path with MITRE techniques corresponding to the inbound and outbound parts of the attack path. This provides automatic mapping to an industry-standard attack framework for auditing, compliance, and faster understanding of all components of the attack.
Richer AI Analyst Investigations
AI Analyst investigations become richer as they enrich existing investigations with malicious hostnames retrieved from PREVENT/ASM. Consequently, this indicates they are more likely to be suspicious and potentially part of an incident.
Heightening Email Security
Darktrace PREVENT/Attack Surface Management informs Darktrace/Email of potential threats, such as domain spoofing. This action heightens sensitivity around these assets and takes action when these spoof domains are used for malicious purposes. Hence, this leads to more accurate decision-making in the email realm, reducing analysis time for individual emails.
Consolidating Insights for Better Response
Assets confirmed as malicious by Darktrace PREVENT/Attack Surface Management automatically become ‘Watched Domains’ in Darktrace/Network. This enhancement enables security teams to consolidate insights from inside the business and externally on the attack surface in a single pane of glass, improving their ability to respond effectively.




